Secure management of biomedical data with cryptographic hardware
- PMID: 22010157
- PMCID: PMC4156282
- DOI: 10.1109/TITB.2011.2171701
Secure management of biomedical data with cryptographic hardware
Abstract
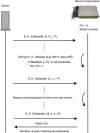
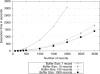
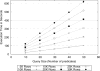
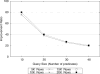
The biomedical community is increasingly migrating toward research endeavors that are dependent on large quantities of genomic and clinical data. At the same time, various regulations require that such data be shared beyond the initial collecting organization (e.g., an academic medical center). It is of critical importance to ensure that when such data are shared, as well as managed, it is done so in a manner that upholds the privacy of the corresponding individuals and the overall security of the system. In general, organizations have attempted to achieve these goals through deidentification methods that remove explicitly, and potentially, identifying features (e.g., names, dates, and geocodes). However, a growing number of studies demonstrate that deidentified data can be reidentified to named individuals using simple automated methods. As an alternative, it was shown that biomedical data could be shared, managed, and analyzed through practical cryptographic protocols without revealing the contents of any particular record. Yet, such protocols required the inclusion of multiple third parties, which may not always be feasible in the context of trust or bandwidth constraints. Thus, in this paper, we introduce a framework that removes the need for multiple third parties by collocating services to store and to process sensitive biomedical data through the integration of cryptographic hardware. Within this framework, we define a secure protocol to process genomic data and perform a series of experiments to demonstrate that such an approach can be run in an efficient manner for typical biomedical investigations.
Figures

References
-
- Khoury M, Rich EC, Randhawa G, Teutsch S, Niederhuber J. Comparative effectiveness research and genomic medicine: An evolving partnership for 21st century medicine. Genet Med. 2009;11(10):707–711. - PubMed
-
- Green E, Guyer M, National Human Genome Research Institute Charting a course for genomic medicine from base pairs to bedside. Nature Genet. 2011;470:204–213. - PubMed
-
- Gurwitz D, Lunshof J, Altman R. A call for the creation of personalized medicine databases. Nature Rev Drug Discov. 2006;5(1):23–26. - PubMed
-
- National Institutes of Health. Policy for sharing of data obtained in NIH supported or conducted genome-wide association studies (GWAS) 2007 Aug; NOT-OD-07-088.
Publication types
MeSH terms
Grants and funding
LinkOut - more resources
Full Text Sources
Other Literature Sources
Research Materials

