iDASH: integrating data for analysis, anonymization, and sharing
- PMID: 22081224
- PMCID: PMC3277627
- DOI: 10.1136/amiajnl-2011-000538
iDASH: integrating data for analysis, anonymization, and sharing
Abstract
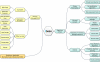
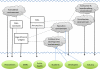
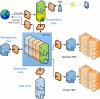
iDASH (integrating data for analysis, anonymization, and sharing) is the newest National Center for Biomedical Computing funded by the NIH. It focuses on algorithms and tools for sharing data in a privacy-preserving manner. Foundational privacy technology research performed within iDASH is coupled with innovative engineering for collaborative tool development and data-sharing capabilities in a private Health Insurance Portability and Accountability Act (HIPAA)-certified cloud. Driving Biological Projects, which span different biological levels (from molecules to individuals to populations) and focus on various health conditions, help guide research and development within this Center. Furthermore, training and dissemination efforts connect the Center with its stakeholders and educate data owners and data consumers on how to share and use clinical and biological data. Through these various mechanisms, iDASH implements its goal of providing biomedical and behavioral researchers with access to data, software, and a high-performance computing environment, thus enabling them to generate and test new hypotheses.
Conflict of interest statement
Figures
References
-
- Kanehisa M, Bork P. Bioinformatics in the post-sequence era. Nat Genet 2003;(33 Suppl):305–10 - PubMed
-
- Lander ES, Linton LM, Birren B, et al. Initial sequencing and analysis of the human genome. Nature 2001;409:860–921 - PubMed
-
- Venter JC, Adams MD, Myers EW, et al. The sequence of the human genome. Science 2001;291:1304–51 - PubMed
Publication types
MeSH terms
Grants and funding
LinkOut - more resources
Full Text Sources
Other Literature Sources

