A systematic review of re-identification attacks on health data
- PMID: 22164229
- PMCID: PMC3229505
- DOI: 10.1371/journal.pone.0028071
A systematic review of re-identification attacks on health data
Erratum in
-
Correction: a systematic review of re-identification attacks on health data.PLoS One. 2015 Apr 16;10(4):e0126772. doi: 10.1371/journal.pone.0126772. eCollection 2015. PLoS One. 2015. PMID: 25880057 Free PMC article. No abstract available.
Abstract
Background: Privacy legislation in most jurisdictions allows the disclosure of health data for secondary purposes without patient consent if it is de-identified. Some recent articles in the medical, legal, and computer science literature have argued that de-identification methods do not provide sufficient protection because they are easy to reverse. Should this be the case, it would have significant and important implications on how health information is disclosed, including: (a) potentially limiting its availability for secondary purposes such as research, and (b) resulting in more identifiable health information being disclosed. Our objectives in this systematic review were to: (a) characterize known re-identification attacks on health data and contrast that to re-identification attacks on other kinds of data, (b) compute the overall proportion of records that have been correctly re-identified in these attacks, and (c) assess whether these demonstrate weaknesses in current de-identification methods.
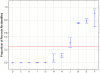
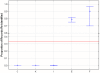
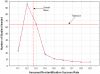
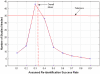
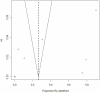
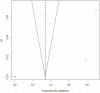
Methods and findings: Searches were conducted in IEEE Xplore, ACM Digital Library, and PubMed. After screening, fourteen eligible articles representing distinct attacks were identified. On average, approximately a quarter of the records were re-identified across all studies (0.26 with 95% CI 0.046-0.478) and 0.34 for attacks on health data (95% CI 0-0.744). There was considerable uncertainty around the proportions as evidenced by the wide confidence intervals, and the mean proportion of records re-identified was sensitive to unpublished studies. Two of fourteen attacks were performed with data that was de-identified using existing standards. Only one of these attacks was on health data, which resulted in a success rate of 0.00013.
Conclusions: The current evidence shows a high re-identification rate but is dominated by small-scale studies on data that was not de-identified according to existing standards. This evidence is insufficient to draw conclusions about the efficacy of de-identification methods.
Conflict of interest statement
Figures
References
-
- Fung BCM, Wang K, Chen R, Yu PS. Privacy-Preserving Data Publishing: A Survey of Recent Developments. ACM Computing Surveys. 2010;42
-
- Perun H, Orr M, Dimitriadis F. 2005. Guide to the Ontario Personal Health Information Protection Act: Irwin Law.
-
- U.S. Department of Health and Human Services. Standards for privacy of individually identifiable health information, final rule, 45 CFR, pt 160–164. 2002. U.S. Department of Health and Human Services. - PubMed
-
- Panel on Research Ethics. 2010. Tri-Council Policy Statement: Ethical Conduct for Research Involving Humans (2nd ed)
-
- Willison DJ, Emerson C, Szala-Meneok KV, Gibson E, Schwartz L, et al. Access to medical records for research purposes: varying perceptions across research ethics boards. J Med Ethics. 2008;34:308–314. - PubMed
Publication types
MeSH terms
Grants and funding
LinkOut - more resources
Full Text Sources
Other Literature Sources

