Design and implementation of a secure wireless mote-based medical sensor network
- PMID: 22454585
- PMCID: PMC3312444
- DOI: 10.3390/s90806273
Design and implementation of a secure wireless mote-based medical sensor network
Abstract
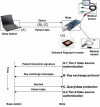
A medical sensor network can wirelessly monitor vital signs of humans, making it useful for long-term health care without sacrificing patient comfort and mobility. For such a network to be viable, its design must protect data privacy and authenticity given that medical data are highly sensitive. We identify the unique security challenges of such a sensor network and propose a set of resource-efficient mechanisms to address these challenges. Our solution includes (1) a novel two-tier scheme for verifying the authenticity of patient data, (2) a secure key agreement protocol to set up shared keys between sensor nodes and base stations, and (3) symmetric encryption/decryption for protecting data confidentiality and integrity. We have implemented the proposed mechanisms on a wireless mote platform, and our results confirm their feasibility.
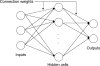
Keywords: elliptic curve cryptography; medical sensor network; neural network; security.
Figures








References
-
- Morris M., Intille S.S., Beaudin J.S. Embedded assessment: Overcoming barriers to early detection with pervasive computing. In: Gellersen H.W., Want R., Schmidt A., editors. Proc. of PERVASIVE 2005. Springer-Verlag; Munich, Germany: May 8–13, 2005. pp. 333–346.
-
- Fischer R., Ohno-Machado L., Curtis D., Greenes R., Stair T., Guttag J. Smart Medical Technologies Summit (SMT) Houston, Texas, USA: Apr, 2004. SMART: Scalable medical alert response technology.
-
- Shnayder V., Chen B.-R., Lorincz K., Fulford-Jones T.R.F., Welsh M. Harvard University; Cambridge, Massachusetts, USA: Apr, 2005. Sensor networks for medical care. Technical Report TR-08-05,
-
- Park C., Chou P.H., Bai Y., Matthews R., Hibbs A. An Ultra-Wearable, Wireless, Low Power ECG Monitoring System. Proceedings of IEEE BioCAS; London, UK. November 2006.
LinkOut - more resources
Full Text Sources
Other Literature Sources

