An improved tamper detection and localization scheme for volumetric DICOM images
- PMID: 22832896
- PMCID: PMC3491158
- DOI: 10.1007/s10278-012-9518-y
An improved tamper detection and localization scheme for volumetric DICOM images
Abstract
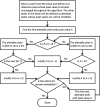
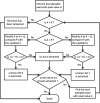
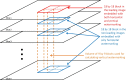
The development of teleradiology brings the convenience of global medical record access along with the concerns over the security of medical images transmitted over the open network. With the prevailing adoption of three-dimensional (3-D) imaging modalities, it is vital to develop a security mechanism to provide large volumes of medical images with privacy and reliability. This paper presents the development of a new and improved method of implementing tamper detection and localization based on a fully reversible digital watermarking scheme for the protection of volumetric DICOM images. This tamper detection and localization method utilizes the 3-D property of volumetric data to achieve much faster processing time at both sender and receiver sides without compromising tamper localization accuracy. The performance of the proposed scheme was evaluated by using sample volumetric DICOM images. Results show that the scheme achieved on average about 65 % and 72 % reduction in watermarking and dewatermarking processing time, respectively. For cases where the images had been tampered, it is possible to detect and localize the tampered areas with improved localization resolution in the images using the scheme.
Figures






References
-
- Digital Imaging and Communications in Medicine (DICOM) Standard. Available at [Online]. Available: http://medical.nema.org/dicom/2006/2006
-
- Macq B, Dewey F. Trusted headers for medical images. Erlangen: DFG VIII-DII Watermarking Workshop; 1999.
-
- Zain JM, Fauzi ARM: Medical image watermarking with tamper detection and recovery. Proc. Engineering in Medicine and Biology Society, 2006 EMBS ‘06 28th Annual International Conference of the IEEE: City, Aug. 30 2006-Sept. 3 2006 Year - PubMed
MeSH terms
LinkOut - more resources
Full Text Sources
Medical

