Compiler optimizations as a countermeasure against side-channel analysis in MSP430-based devices
- PMID: 22969383
- PMCID: PMC3436012
- DOI: 10.3390/s120607994
Compiler optimizations as a countermeasure against side-channel analysis in MSP430-based devices
Abstract
Ambient Intelligence (AmI) requires devices everywhere, dynamic and massively distributed networks of low-cost nodes that, among other data, manage private information or control restricted operations. MSP430, a 16-bit microcontroller, is used in WSN platforms, as the TelosB. Physical access to devices cannot be restricted, so attackers consider them a target of their malicious attacks in order to obtain access to the network. Side-channel analysis (SCA) easily exploits leakages from the execution of encryption algorithms that are dependent on critical data to guess the key value. In this paper we present an evaluation framework that facilitates the analysis of the effects of compiler and backend optimizations on the resistance against statistical SCA. We propose an optimization-based software countermeasure that can be used in current low-cost devices to radically increase resistance against statistical SCA, analyzed with the new framework.
Keywords: MSP430; compiler optimization; embedded system security; hiding countermeasure; side-channel attacks.
Figures
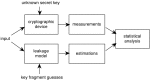

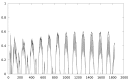
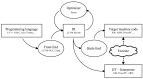


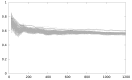

References
-
- Ducatel K., Bogdanowicz M., Scapolo F., Leijten J., Burgelman J.-C. Scenarios for Ambient Intelligence in 2010. ISTAG; 2001. Technical Report. Available online: ftp://ftp.cordis.europa.eu/pub/ist/docs/istagscenarios.pdf (accessed on 8 June 2012)
-
- Friedewald M., Vildjiounaite E., Punie Y., Wright D. Privacy, identity and security in ambient intelligence: A scenario analysis. Telemat. Inf. 2007;24:15–29.
-
- Portilla J., de Castro A., de la Torre E., Riesgo T. A modular architecture for nodes in wireless sensor networks. J. Univ.Comput. Sci. 2006;12:328–339.
-
- Jara A., Zamora M., Skarmeta A. An internet of things-based personal device for diabetes therapy management in ambient assisted living (AAL) Pers. Ubiquitous Comput. 2011;15:431–440. doi: 10.1007/s00779-010-0353-1. - DOI
-
- Tentori M., Favela J., González V.M. Quality of Privacy (QoP) for the design of ubiquitous healthcare applications. J. Univ. Comput. Sci. 2006;12:252–269.
Publication types
LinkOut - more resources
Full Text Sources
Other Literature Sources

