Exploring the limits of community detection strategies in complex networks
- PMID: 23860510
- PMCID: PMC3713530
- DOI: 10.1038/srep02216
Exploring the limits of community detection strategies in complex networks
Abstract
The characterization of network community structure has profound implications in several scientific areas. Therefore, testing the algorithms developed to establish the optimal division of a network into communities is a fundamental problem in the field. We performed here a highly detailed evaluation of community detection algorithms, which has two main novelties: 1) using complex closed benchmarks, which provide precise ways to assess whether the solutions generated by the algorithms are optimal; and, 2) A novel type of analysis, based on hierarchically clustering the solutions suggested by multiple community detection algorithms, which allows to easily visualize how different are those solutions. Surprise, a global parameter that evaluates the quality of a partition, confirms the power of these analyses. We show that none of the community detection algorithms tested provide consistently optimal results in all networks and that Surprise maximization, obtained by combining multiple algorithms, obtains quasi-optimal performances in these difficult benchmarks.
Figures



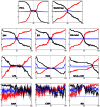

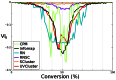
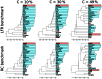

References
-
- Dorogovtsev S. N. & Mendes J. F. F. Evolution of Networks: From Biological Nets to the Internet and WWW. (Oxford University Press: 2003).
-
- Newman M. E. J. Networks: An Introduction. (Oxford University Press: 2010).
-
- Fortunato S. Community detection in graphs. Phys. Rep. 486, 75–174 (2010).
-
- Aldecoa R. & Marín I. Closed benchmarks for network community structure characterization. Phys. Rev. E 85, 026109 (2012). - PubMed
Publication types
LinkOut - more resources
Full Text Sources
Other Literature Sources

