Crowdsourcing contest dilemma
- PMID: 25142518
- PMCID: PMC4233728
- DOI: 10.1098/rsif.2014.0532
Crowdsourcing contest dilemma
Abstract
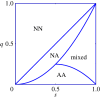
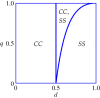
Crowdsourcing offers unprecedented potential for solving tasks efficiently by tapping into the skills of large groups of people. A salient feature of crowdsourcing--its openness of entry--makes it vulnerable to malicious behaviour. Such behaviour took place in a number of recent popular crowdsourcing competitions. We provide game-theoretic analysis of a fundamental trade-off between the potential for increased productivity and the possibility of being set back by malicious behaviour. Our results show that in crowdsourcing competitions malicious behaviour is the norm, not the anomaly--a result contrary to the conventional wisdom in the area. Counterintuitively, making the attacks more costly does not deter them but leads to a less desirable outcome. These findings have cautionary implications for the design of crowdsourcing competitions.
Keywords: Prisoner's Dilemma; crowdsourcing; game theory.
© 2014 The Author(s) Published by the Royal Society. All rights reserved.
Figures
References
-
- Howe J. 2006. The rise of crowdsourcing. Wired Mag. 14, 1–4.
-
- Von Ahn L. 2006. Games with a purpose. Computer 39, 92–94. (10.1109/MC.2006.196) - DOI
-
- Horowitz D, Kamvar SD. 2010. The anatomy of a large-scale social search engine. In Proc. 19th ACM Int. Conf. on World Wide Web, pp. 431–440. New York, NY: ACM. (10.1145/1772690.1772735) - DOI
Publication types
MeSH terms
LinkOut - more resources
Full Text Sources
Other Literature Sources