A Probabilistic Approach to Mitigate Composition Attacks on Privacy in Non-Coordinated Environments
- PMID: 25598581
- PMCID: PMC4295121
- DOI: 10.1016/j.knosys.2014.04.019
A Probabilistic Approach to Mitigate Composition Attacks on Privacy in Non-Coordinated Environments
Abstract
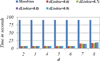
Organizations share data about individuals to drive business and comply with law and regulation. However, an adversary may expose confidential information by tracking an individual across disparate data publications using quasi-identifying attributes (e.g., age, geocode and sex) associated with the records. Various studies have shown that well-established privacy protection models (e.g., k-anonymity and its extensions) fail to protect an individual's privacy against this "composition attack". This type of attack can be thwarted when organizations coordinate prior to data publication, but such a practice is not always feasible. In this paper, we introduce a probabilistic model called (d, α)-linkable, which mitigates composition attack without coordination. The model ensures that d confidential values are associated with a quasi-identifying group with a likelihood of α. We realize this model through an efficient extension to k-anonymization and use extensive experiments to show our strategy significantly reduces the likelihood of a successful composition attack and can preserve more utility than alternative privacy models, such as differential privacy.
Keywords: Anonymization; Composition attack; Data publication; Databases; Privacy.
Figures












References
-
- Aggarwal Charu C, Yu Philip S. A condensation approach to privacy preserving data mining. Proceedings of the 9th International Conference on Extending Database Technology; Heraklion, Crete; Greece. 2004. pp. 183–199.
-
- Cebul Randall D, Rebitzer James B, Taylor Lowell J, Votruba Mark. Organizational fragmentation and care quality in the U.S. health care system. Working Paper 14212, National Bureau of Economic Research. 2008 Aug - PubMed
-
- Chow Richard, Golle Philippe, Staddon Jessica. Detecting privacy leaks using corpus-based association rules. Proceedings of the 14th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining; Las Vegas; Nevada, U.S.. 2008. pp. 893–901.
-
- Domingo-Ferrer Josep, Torra Vicenҫ. Ordinal, continuous and heterogeneous k-anonymity through microaggregation. Data Mining and Knowledge Discovery. 2005;11(2):195–212.
-
- Domingo-Ferrer Josep, González-Nicolás Úrsula. Hybrid microdata using microaggregation. Information Sciences. 2010;180(15):2834–2844.
Grants and funding
LinkOut - more resources
Full Text Sources
Other Literature Sources
