Exploring the Far Side of Mobile Health: Information Security and Privacy of Mobile Health Apps on iOS and Android
- PMID: 25599627
- PMCID: PMC4319144
- DOI: 10.2196/mhealth.3672
Exploring the Far Side of Mobile Health: Information Security and Privacy of Mobile Health Apps on iOS and Android
Abstract
Background: Mobile health (mHealth) apps aim at providing seamless access to tailored health information technology and have the potential to alleviate global health burdens. Yet, they bear risks to information security and privacy because users need to reveal private, sensitive medical information to redeem certain benefits. Due to the plethora and diversity of available mHealth apps, implications for information security and privacy are unclear and complex.
Objective: The objective of this study was to establish an overview of mHealth apps offered on iOS and Android with a special focus on potential damage to users through information security and privacy infringements.
Methods: We assessed apps available in English and offered in the categories "Medical" and "Health & Fitness" in the iOS and Android App Stores. Based on the information retrievable from the app stores, we established an overview of available mHealth apps, tagged apps to make offered information machine-readable, and clustered the discovered apps to identify and group similar apps. Subsequently, information security and privacy implications were assessed based on health specificity of information available to apps, potential damage through information leaks, potential damage through information manipulation, potential damage through information loss, and potential value of information to third parties.
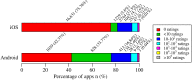
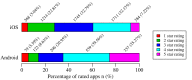
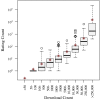
Results: We discovered 24,405 health-related apps (iOS; 21,953; Android; 2452). Absence or scarceness of ratings for 81.36% (17,860/21,953) of iOS and 76.14% (1867/2452) of Android apps indicates that less than a quarter of mHealth apps are in more or less widespread use. Clustering resulted in 245 distinct clusters, which were consolidated into 12 app archetypes grouping clusters with similar assessments of potential damage through information security and privacy infringements. There were 6426 apps that were excluded during clustering. The majority of apps (95.63%, 17,193/17,979; of apps) pose at least some potential damage through information security and privacy infringements. There were 11.67% (2098/17,979) of apps that scored the highest assessments of potential damages.
Conclusions: Various kinds of mHealth apps collect and offer critical, sensitive, private medical information, calling for a special focus on information security and privacy of mHealth apps. In order to foster user acceptance and trust, appropriate security measures and processes need to be devised and employed so that users can benefit from seamlessly accessible, tailored mHealth apps without exposing themselves to the serious repercussions of information security and privacy infringements.
Keywords: data security; health information technology; mobile apps; mobile health; patient privacy; software and application security.
Conflict of interest statement
Conflicts of Interest: None declared.
Figures


References
-
- Collins F. Sci Am. 2012. Jul 10, [2014-12-29]. The real promise of mobile health apps http://www.scientificamerican.com/article/real-promise-mobile-health-apps/
-
- Kumar S, Nilsen W, Pavel M, Srivastava M. Mobile health: Revolutionizing healthcare through transdisciplinary research. Computer. 2013 Jan;46(1):28–35. doi: 10.1109/MC.2012.392. - DOI
-
- Mechael PN. The case for mHealth in developing countries. Innovations: Technology, Governance, Globalization. 2009 Jan;4(1):103–118. doi: 10.1162/itgg.2009.4.1.103. - DOI
-
- Istepanian R, Jovanov E, Zhang YT. Introduction to the special section on M-Health: Beyond seamless mobility and global wireless health-care connectivity. IEEE Trans Inf Technol Biomed. 2004 Dec;8(4):405–414. - PubMed
LinkOut - more resources
Full Text Sources
Other Literature Sources