Computational Fact Checking from Knowledge Networks
- PMID: 26083336
- PMCID: PMC4471100
- DOI: 10.1371/journal.pone.0128193
Computational Fact Checking from Knowledge Networks
Erratum in
-
Correction: Computational Fact Checking from Knowledge Networks.PLoS One. 2015 Oct 27;10(10):e0141938. doi: 10.1371/journal.pone.0141938. eCollection 2015. PLoS One. 2015. PMID: 26505751 Free PMC article. No abstract available.
Abstract
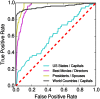
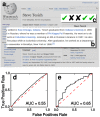
Traditional fact checking by expert journalists cannot keep up with the enormous volume of information that is now generated online. Computational fact checking may significantly enhance our ability to evaluate the veracity of dubious information. Here we show that the complexities of human fact checking can be approximated quite well by finding the shortest path between concept nodes under properly defined semantic proximity metrics on knowledge graphs. Framed as a network problem this approach is feasible with efficient computational techniques. We evaluate this approach by examining tens of thousands of claims related to history, entertainment, geography, and biographical information using a public knowledge graph extracted from Wikipedia. Statements independently known to be true consistently receive higher support via our method than do false ones. These findings represent a significant step toward scalable computational fact-checking methods that may one day mitigate the spread of harmful misinformation.
Conflict of interest statement
Figures

References
-
- Mendoza M, Poblete B, Castillo C. Twitter Under Crisis: Can We Trust What We RT? In: Proceedings of the First Workshop on Social Media Analytics SOMA’10. New York, NY, USA: ACM; 2010. p. 71–79.
-
- Ratkiewicz J, Conover M, Meiss M, GonÇalves B, Flammini A, Menczer F. Detecting and Tracking Political Abuse in Social Media In: Proceedings of the Fifth International AAAI Conference on Weblogs and Social Media. Barcelona, Spain: AAAI; 2011.
-
- Cranor LF, LaMacchia BA. Spam! Commun ACM. 1998. August;41(8):74–83. 10.1145/280324.280336 - DOI
-
- Jagatic TN, Johnson NA, Jakobsson M, Menczer F. Social Phishing. Commun ACM. 2007. October;50(10):94–100. 10.1145/1290958.1290968 - DOI
-
- Friggeri A, Adamic LA, Eckles D, Cheng J. Rumor Cascades. In: Proceedings of the Eighth International AAAI Conference on Weblogs and Social Media. Ann Arbor, MI: AAAI; 2014.
Publication types
MeSH terms
Grants and funding
LinkOut - more resources
Full Text Sources
Other Literature Sources

