Quantum key distribution over 120 km using ultrahigh purity single-photon source and superconducting single-photon detectors
- PMID: 26404010
- PMCID: PMC4585911
- DOI: 10.1038/srep14383
Quantum key distribution over 120 km using ultrahigh purity single-photon source and superconducting single-photon detectors
Abstract
Advances in single-photon sources (SPSs) and single-photon detectors (SPDs) promise unique applications in the field of quantum information technology. In this paper, we report long-distance quantum key distribution (QKD) by using state-of-the-art devices: a quantum-dot SPS (QD SPS) emitting a photon in the telecom band of 1.5 μm and a superconducting nanowire SPD (SNSPD). At the distance of 100 km, we obtained the maximal secure key rate of 27.6 bps without using decoy states, which is at least threefold larger than the rate obtained in the previously reported 50-km-long QKD experiment. We also succeeded in transmitting secure keys at the rate of 0.307 bps over 120 km. This is the longest QKD distance yet reported by using known true SPSs. The ultralow multiphoton emissions of our SPS and ultralow dark count of the SNSPD contributed to this result. The experimental results demonstrate the potential applicability of QD SPSs to practical telecom QKD networks.
Figures

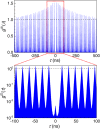
 = 0.05 at the repetition rate of 62.5 MHz. The lower trace is a magnification of the central part of the upper trace around τ ~ 0, and g(2)(0) is plotted on a logarithmic scale.
= 0.05 at the repetition rate of 62.5 MHz. The lower trace is a magnification of the central part of the upper trace around τ ~ 0, and g(2)(0) is plotted on a logarithmic scale.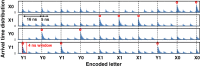


References
-
- Bennett C. H. & Brassard G. Quantum cryptography: Public key distribution and coin tossing. in Proc. IEEE International Conference of Computer Systems and Signal Processing, 175–179 (Bangalore, India, 1984).
-
- Bennett C. H., Bessette F., Brassard G., Salvail L. & Smolin J. Experimental quantum cryptography. J. Cryptol. 5, 3–28 (1991).
-
- Zbinden H. Experimental Quantum Cryptography. in Introduction to quantum computation and information edited by Lo H.–K. et al. pp. 120 (World Scientific, 1998).
-
- Ekart A., Gisin N., Huttner B., Inamori H. & Weinfurter H. Quantum Cryptography. in The Physics of Quantum Information edited by Bouwmeester D. et al. pp. 15 (Springer, 2000).
-
- Gisin N., Ribordy G., Tittel W. & Zbinden H. Quantum cryptography. Rev. Mod. Phys. 74, 145–195 (2002).
Publication types
LinkOut - more resources
Full Text Sources
Other Literature Sources

