Problems in using p-curve analysis and text-mining to detect rate of p-hacking and evidential value
- PMID: 26925335
- PMCID: PMC4768688
- DOI: 10.7717/peerj.1715
Problems in using p-curve analysis and text-mining to detect rate of p-hacking and evidential value
Abstract
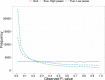
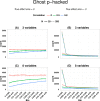
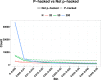
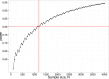
Background. The p-curve is a plot of the distribution of p-values reported in a set of scientific studies. Comparisons between ranges of p-values have been used to evaluate fields of research in terms of the extent to which studies have genuine evidential value, and the extent to which they suffer from bias in the selection of variables and analyses for publication, p-hacking. Methods. p-hacking can take various forms. Here we used R code to simulate the use of ghost variables, where an experimenter gathers data on several dependent variables but reports only those with statistically significant effects. We also examined a text-mined dataset used by Head et al. (2015) and assessed its suitability for investigating p-hacking. Results. We show that when there is ghost p-hacking, the shape of the p-curve depends on whether dependent variables are intercorrelated. For uncorrelated variables, simulated p-hacked data do not give the "p-hacking bump" just below .05 that is regarded as evidence of p-hacking, though there is a negative skew when simulated variables are inter-correlated. The way p-curves vary according to features of underlying data poses problems when automated text mining is used to detect p-values in heterogeneous sets of published papers. Conclusions. The absence of a bump in the p-curve is not indicative of lack of p-hacking. Furthermore, while studies with evidential value will usually generate a right-skewed p-curve, we cannot treat a right-skewed p-curve as an indicator of the extent of evidential value, unless we have a model specific to the type of p-values entered into the analysis. We conclude that it is not feasible to use the p-curve to estimate the extent of p-hacking and evidential value unless there is considerable control over the type of data entered into the analysis. In particular, p-hacking with ghost variables is likely to be missed.
Keywords: Correlation; Ghost variables; Power; Reproducibility; Simulation; Text-mining; p-curve; p-hacking.
Conflict of interest statement
Dorothy V. Bishop is an Academic Advisor and an Academic Editor for PeerJ.
Figures
References
-
- Academy of Medical Sciences. BBSRC. MRC. Wellcome Trust . Reproducibility and reliability of biomedical research: improving research practice. London: Academy of Medical Sciences; 2015. Available at http://www.acmedsci.ac.uk/policy/policy-projects/reproducibility-and-rel...
-
- Begg CB, Berlin JA. Publication bias: a problem in interpreting medical data. Journal of the Royal Statistical Society: Series A. 1988;151(3):419–463. doi: 10.2307/2982993. - DOI
-
- Chernick MR, Liu CY. The saw-toothed behavior of power versus sample size and software solutions. The American Statistician. 2002;56:149–155. doi: 10.1198/000313002317572835. - DOI
Grants and funding
LinkOut - more resources
Full Text Sources
Other Literature Sources

