Trusted Autonomy and Cognitive Cyber Symbiosis: Open Challenges
- PMID: 27257440
- PMCID: PMC4867784
- DOI: 10.1007/s12559-015-9365-5
Trusted Autonomy and Cognitive Cyber Symbiosis: Open Challenges
Abstract
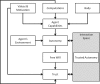
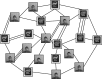
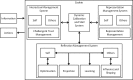
This paper considers two emerging interdisciplinary, but related topics that are likely to create tipping points in advancing the engineering and science areas. Trusted Autonomy (TA) is a field of research that focuses on understanding and designing the interaction space between two entities each of which exhibits a level of autonomy. These entities can be humans, machines, or a mix of the two. Cognitive Cyber Symbiosis (CoCyS) is a cloud that uses humans and machines for decision-making. In CoCyS, human-machine teams are viewed as a network with each node comprising humans (as computational machines) or computers. CoCyS focuses on the architecture and interface of a Trusted Autonomous System. This paper examines these two concepts and seeks to remove ambiguity by introducing formal definitions for these concepts. It then discusses open challenges for TA and CoCyS, that is, whether a team made of humans and machines can work in fluid, seamless harmony.
Keywords: Autonomy; Cognitive Cyber Symbiosis; Human–machine teaming; Trust; Trusted Autonomous System; Trusted Autonomy.
Figures





References
-
- Chandrasekaran B, Conrad JM. Human–robot collaboration: a survey. In: SoutheastCon 2015, IEEE 2015. p. 1–8.
-
- Huhns MN, Buell DA. Trusted autonomy. IEEE Internet Comput. 2002;3:92–95. doi: 10.1109/MIC.2002.1003138. - DOI
-
- Morrison EW, Robinson SL. When employees feel betrayed: a model of how psychological contract violation develops. Acad Manag Rev. 1997;22(1):226–256.
-
- Deutsch M. The resolution of conflict: constructive and destructive processes. New Haven: Yale University Press; 1977.
Publication types
LinkOut - more resources
Full Text Sources
Other Literature Sources
