A Hybrid Scheme for Fine-Grained Search and Access Authorization in Fog Computing Environment
- PMID: 28629131
- PMCID: PMC5492313
- DOI: 10.3390/s17061423
A Hybrid Scheme for Fine-Grained Search and Access Authorization in Fog Computing Environment
Abstract
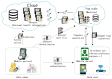
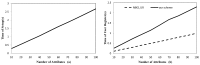
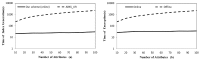
In the fog computing environment, the encrypted sensitive data may be transferred to multiple fog nodes on the edge of a network for low latency; thus, fog nodes need to implement a search over encrypted data as a cloud server. Since the fog nodes tend to provide service for IoT applications often running on resource-constrained end devices, it is necessary to design lightweight solutions. At present, there is little research on this issue. In this paper, we propose a fine-grained owner-forced data search and access authorization scheme spanning user-fog-cloud for resource constrained end users. Compared to existing schemes only supporting either index encryption with search ability or data encryption with fine-grained access control ability, the proposed hybrid scheme supports both abilities simultaneously, and index ciphertext and data ciphertext are constructed based on a single ciphertext-policy attribute based encryption (CP-ABE) primitive and share the same key pair, thus the data access efficiency is significantly improved and the cost of key management is greatly reduced. Moreover, in the proposed scheme, the resource constrained end devices are allowed to rapidly assemble ciphertexts online and securely outsource most of decryption task to fog nodes, and mediated encryption mechanism is also adopted to achieve instantaneous user revocation instead of re-encrypting ciphertexts with many copies in many fog nodes. The security and the performance analysis show that our scheme is suitable for a fog computing environment.
Keywords: attribute-based encryption; cloud computing; fog computing; mediated encryption; online/offline encryption; searchable encryption.
Conflict of interest statement
The authors declare no conflict of interest.
Figures

References
-
- Bonomi F., Milito R., Zhu J., Addepalli S. Fog Computing and its Role in the Internet of Things; Proceedings of the first edition of the MCC workshop on Mobile cloud computing; Helsinki, Finland. 17 August 2012; pp. 13–16.
-
- Stojmenovic I., Wen S. The Fog computing paradigm: Scenarios and security issues; Proceedings of the Federated Conference on Computer Science and Information Systems; Warsaw, Poland. 7–10 September 2014; pp. 1–8.
-
- Yi S., Li C., Li Q. A Survey of Fog Computing: Concepts, Applications and Issues; Proceedings of the 2015 Workshop on Mobile Big Data; Hangzhou, China. 21 June 2015; pp. 37–42. - DOI
-
- Goyal V., Pandey O., Sahai A., Waters B. Attribute-based encryption for fine-grained access control of encrypted data; Proceedings of the ACM Conference on Computer and Communications Security, CCS 2006; Alexandria, VA, USA. 30 October–3 November 2006; pp. 89–98.
-
- Bethencourt J., Sahai A., Waters B. Ciphertext-Policy Attribute-Based Encryption; Procededings of the IEEE Symposium on Security and Privacy, 2007; Berkeley, CA, USA. 20–23 May 2007; pp. 321–334.
LinkOut - more resources
Full Text Sources
Other Literature Sources
Miscellaneous

