MPH-M, AODV-M and DSR-M Performance Evaluation under Jamming Attacks
- PMID: 28678180
- PMCID: PMC5539809
- DOI: 10.3390/s17071573
MPH-M, AODV-M and DSR-M Performance Evaluation under Jamming Attacks
Abstract
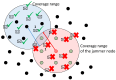
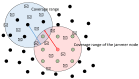
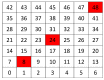
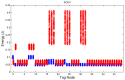
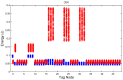
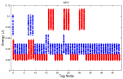
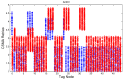
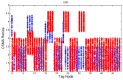
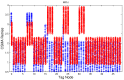
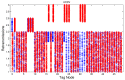
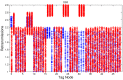
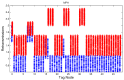
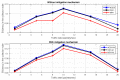
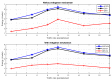
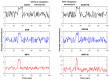
In this work, we present the design of a mitigation scheme for jamming attacks integrated to the routing protocols MPH, AODV, and DSR. The resulting protocols are named MPH-M (Multi-Parent Hierarchical - Modified), AODV-M (Ad hoc On Demand Distance Vector - Modified), and DSR-M (Dynamic Source Routing - Modified). For the mitigation algorithm, if the detection algorithm running locally in each node produces a positive result then the node is isolated; second, the routing protocol adapts their paths avoiding the isolated nodes. We evaluated how jamming attacks affect different metrics for all these modified protocols. The metrics we employ to detect jamming attack are number of packet retransmissions, number of CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance) retries while waiting for an idle channel and the energy wasted by the node. The metrics to evaluate the performance of the modified routing protocols are the throughput and resilience of the system and the energy used by the nodes. We evaluated all the modified protocols when the attacker position was set near, middle and far of the collector node. The results of our evaluation show that performance for MPH-M is much better than AODV-M and DSR-M. For example, the node energy for MPH-M is 138.13% better than AODV-M and 126.07% better than DSR-M. Moreover, we also find that MPH-M benefits much more of the mitigation scheme than AODV-M and DSR-M. For example, the node energy consumption is 34.61% lower for MPH-M and only 3.92% and 3.42% for AODV-M and DSR-M, respectively. On throughput, the MPH protocol presents a packet reception efficiency at the collector node of 16.4% on to AODV and DSR when there is no mitigation mechanism. Moreover, MPH-M has an efficiency greater than 7.7% with respect to AODV-M and DSR-M when there is a mitigation scheme. In addition, we have that with the mitigation mechanism AODV-M and DSR-M do not present noticeable modification. However, MPH-M improves its efficiency by 8.4%. We also measure the resilience of these algorithms from the average packet re-transmissions perspective, and we find that MPH-M has around a 15% lower change rate than AODV-M and DSR-M. The MPH-M recovery time is 5 s faster than AODV-M and 2 s faster than DSR-M.
Keywords: Wireless Sensor Networks; jamming; routing algorithms.
Conflict of interest statement
The authors declare no conflict of interest.
Figures
References
-
- Akyildiz I.F., Su W.J., Sankarasubramaniam Y., Cayirci E. Wireless sensor networks: A survey. Comput. Netw. 2002;38:393–422. doi: 10.1016/S1389-1286(01)00302-4. - DOI
-
- IEEE . IEEE Standard 802.15.4-2006 (Revision of IEEE Standard 802.15.4-2003) IEEE Computer Society; New York, NY, USA: 2006. Wireless medium access control (MAC) and physical layer (PHY) specifications for low-rate wireless personal area networks (WPANs) pp. 1–305.
-
- Del-Valle-Soto C., Mex-Perera C., Olmedo O., Orozco-Lugo A., Galván-Tejada G., Lara M. An efficient Multi-Parent Hierarchical Routing Protocol for WSNs; Proceedings of the Wireless Telecommunications Symposium (WTS); Washington, DC, USA. 9–11 April 2014; pp. 1–8.
-
- Perkins C., Royer E. Ad-hoc on-demand distance vector routing; Proceedings of the IEEE Workshop on Mobile Computing Systems and Applications, WMCSA; New Orleans, LA, USA. 25–26 February 1999; pp. 90–100.
-
- Maltz D., Broch J., Jetcheva J., Johnson D. The effects of on-demand behavior in routing protocols for multihop wireless ad hoc networks. IEEE J. Sel. Areas Commun. 1999;17:1439–1453. doi: 10.1109/49.779925. - DOI
LinkOut - more resources
Full Text Sources
Other Literature Sources

