Tamper-Resistant Mobile Health Using Blockchain Technology
- PMID: 28747296
- PMCID: PMC5550736
- DOI: 10.2196/mhealth.7938
Tamper-Resistant Mobile Health Using Blockchain Technology
Abstract
Background: Digital health technologies, including telemedicine, mobile health (mHealth), and remote monitoring, are playing a greater role in medical practice. Safe and accurate management of medical information leads to the advancement of digital health, which in turn results in a number of beneficial effects. Furthermore, mHealth can help lower costs by facilitating the delivery of care and connecting people to their health care providers. Mobile apps help empower patients and health care providers to proactively address medical conditions through near real-time monitoring and treatment, regardless of the location of the patient or the health care provider. Additionally, mHealth data are stored in servers, and consequently, data management that prevents all forms of manipulation is crucial for both medical practice and clinical trials.
Objective: The aim of this study was to develop and evaluate a tamper-resistant mHealth system using blockchain technology, which enables trusted and auditable computing using a decentralized network.
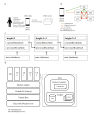
Methods: We developed an mHealth system for cognitive behavioral therapy for insomnia using a smartphone app. The volunteer data collected with the app were stored in JavaScript Object Notation format and sent to the blockchain network. Thereafter, we evaluated the tamper resistance of the data against the inconsistencies caused by artificial faults.
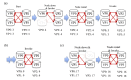
Results: Electronic medical records collected using smartphones were successfully sent to a private Hyperledger Fabric blockchain network. We verified the data update process under conditions where all the validating peers were running normally. The mHealth data were successfully updated under network faults. We further ensured that any electronic health record registered to the blockchain network was resistant to tampering and revision. The mHealth data update was compatible with tamper resistance in the blockchain network.
Conclusions: Blockchain serves as a tamperproof system for mHealth. Combining mHealth with blockchain technology may provide a novel solution that enables both accessibility and data transparency without a third party such as a contract research organization.
Keywords: cognitive therapy; computer security; electronic health records; sleep; telemedicine.
©Daisuke Ichikawa, Makiko Kashiyama, Taro Ueno. Originally published in JMIR Mhealth and Uhealth (http://mhealth.jmir.org), 26.07.2017.
Conflict of interest statement
Conflicts of Interest: The authors are members of Sustainable Medicine, Inc.
Figures



References
-
- Peter S. Ama-assn. 2016. [2017-07-19]. Integration of mobile health applications and devices into practice https://www.ama-assn.org/sites/default/files/media-browser/public/about-... 6s4Fz8Rtm.
-
- Zhang R, Liu L. Security models and requirements for healthcare application clouds. IEEE 3rd International Conference on Cloud Computing; 2010; Miami, FL. 2010. - DOI
-
- Rodrigues JJ, de la Torre I, Fernández G, López-Coronado M. Analysis of the security and privacy requirements of cloud-based electronic health records systems. J Med Internet Res. 2013 Aug 21;15(8):e186. doi: 10.2196/jmir.2494. http://paperpile.com/b/RUDrOC/yFzwy - DOI - PMC - PubMed
-
- Nugent T, Upton D, Cimpoesu M. Improving data transparency in clinical trials using blockchain smart contracts. F1000Res. 2016;5:2541. doi: 10.12688/f1000research.9756.1. https://f1000research.com/articles/10.12688/f1000research.9756.1/doi - DOI - DOI - PMC - PubMed
-
- Crosby M, Nachiappan. Pattanayak P, Verma S, Kalyanaraman V. Berkeley. [2017-05-27]. BlockChain technology: beyond Bitcoin http://scet.berkeley.edu/wp-content/uploads/AIR-2016-Blockchain.pdf 6qlaKudww.
LinkOut - more resources
Full Text Sources
Other Literature Sources