On Efficient Deployment of Wireless Sensors for Coverage and Connectivity in Constrained 3D Space
- PMID: 28994749
- PMCID: PMC5677243
- DOI: 10.3390/s17102304
On Efficient Deployment of Wireless Sensors for Coverage and Connectivity in Constrained 3D Space
Abstract
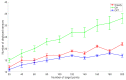
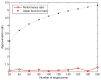
Sensor networks have been used in a rapidly increasing number of applications in many fields. This work generalizes a sensor deployment problem to place a minimum set of wireless sensors at candidate locations in constrained 3D space to k-cover a given set of target objects. By exhausting the combinations of discreteness/continuousness constraints on either sensor locations or target objects, we formulate four classes of sensor deployment problems in 3D space: deploy sensors at Discrete/Continuous Locations (D/CL) to cover Discrete/Continuous Targets (D/CT). We begin with the design of an approximate algorithm for DLDT and then reduce DLCT, CLDT, and CLCT to DLDT by discretizing continuous sensor locations or target objects into a set of divisions without sacrificing sensing precision. Furthermore, we consider a connected version of each problem where the deployed sensors must form a connected network, and design an approximation algorithm to minimize the number of deployed sensors with connectivity guarantee. For performance comparison, we design and implement an optimal solution and a genetic algorithm (GA)-based approach. Extensive simulation results show that the proposed deployment algorithms consistently outperform the GA-based heuristic and achieve a close-to-optimal performance in small-scale problem instances and a significantly superior overall performance than the theoretical upper bound.
Keywords: approximation algorithm; k-coverage; network connectivity; sensor deployment.
Conflict of interest statement
The authors declare no conflict of interest.
Figures





Similar articles
-
On the deployment of a connected sensor network for confident information coverage.Sensors (Basel). 2015 May 14;15(5):11277-94. doi: 10.3390/s150511277. Sensors (Basel). 2015. PMID: 26007715 Free PMC article.
-
On Connected Target k-Coverage in Heterogeneous Wireless Sensor Networks.Sensors (Basel). 2016 Jan 15;16(1):104. doi: 10.3390/s16010104. Sensors (Basel). 2016. PMID: 26784201 Free PMC article.
-
Target Coverage in Wireless Sensor Networks with Probabilistic Sensors.Sensors (Basel). 2016 Aug 27;16(9):1372. doi: 10.3390/s16091372. Sensors (Basel). 2016. PMID: 27618902 Free PMC article.
-
Wireless Sensor Network Optimization: Multi-Objective Paradigm.Sensors (Basel). 2015 Jul 20;15(7):17572-620. doi: 10.3390/s150717572. Sensors (Basel). 2015. PMID: 26205271 Free PMC article. Review.
-
Distributed electrochemical sensors: recent advances and barriers to market adoption.Anal Bioanal Chem. 2018 Jul;410(17):4077-4089. doi: 10.1007/s00216-018-1104-9. Epub 2018 May 28. Anal Bioanal Chem. 2018. PMID: 29806065 Review.
Cited by
-
Efficient Graphical Algorithm of Sensor Distribution and Air Volume Reconstruction for a Smart Mine Ventilation Network.Sensors (Basel). 2022 Mar 8;22(6):2096. doi: 10.3390/s22062096. Sensors (Basel). 2022. PMID: 35336265 Free PMC article.
References
-
- Chakrabarty K., Iyengar S., Qi H., Cho E. Grid coverage for surveillance and target location in DSNs. IEEE Trans. Comput. 2002;51:1448–1453. doi: 10.1109/TC.2002.1146711. - DOI
-
- Vales-Alonso J., Parrado-García F., López-Matencio P., Alcaraz J., González-Castañob F.J. On the optimal random deployment of wireless sensor networks in non-homogeneous scenarios. Ad Hoc Netw. 2013;11:846–860. doi: 10.1016/j.adhoc.2012.10.001. - DOI
-
- Xia M., Dong Y., Lu D., Xue P., Liu G. A Wireless Sensor System for Long-Term Microclimate Monitoring in Wildland Cultural Heritage Sites; Proceedings of the IEEE International Symposium on Parallel and Distributed Processing with Applications; Sydney, NSW, Australia. 10–12 December 2008; pp. 207–214.
-
- Jooa J., Yimb J., Leec C.K. Protecting cultural heritage tourism sites with the ubiquitous sensor network. J. Sustain. Tour. 2009;17:397–406. doi: 10.1080/09669580802582498. - DOI
-
- Lin Y., Wu Q. Approximate Algorithms for Sensor Deployment with k-coverage in Constrained 3D Space; Proceedings of the 16th International Conference on Parallel and Distributed Systems; Shanghai, China. 8–10 December 2010.
LinkOut - more resources
Full Text Sources
Other Literature Sources

