Blockchain distributed ledger technologies for biomedical and health care applications
- PMID: 29016974
- PMCID: PMC6080687
- DOI: 10.1093/jamia/ocx068
Blockchain distributed ledger technologies for biomedical and health care applications
Abstract
Objectives: To introduce blockchain technologies, including their benefits, pitfalls, and the latest applications, to the biomedical and health care domains.
Target audience: Biomedical and health care informatics researchers who would like to learn about blockchain technologies and their applications in the biomedical/health care domains.
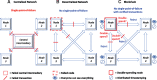
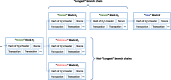
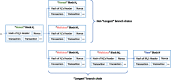
Scope: The covered topics include: (1) introduction to the famous Bitcoin crypto-currency and the underlying blockchain technology; (2) features of blockchain; (3) review of alternative blockchain technologies; (4) emerging nonfinancial distributed ledger technologies and applications; (5) benefits of blockchain for biomedical/health care applications when compared to traditional distributed databases; (6) overview of the latest biomedical/health care applications of blockchain technologies; and (7) discussion of the potential challenges and proposed solutions of adopting blockchain technologies in biomedical/health care domains.
Keywords: blockchain; distributed ledger technology; health information exchange; interoperability; security.
© The Author 2017. Published by Oxford University Press on behalf of the American Medical Informatics Association.
Figures



References
-
- Nakamoto S. Bitcoin: A peer-to-peer electronic cash system. https://bitcoin.org/bitcoin.pdf. 2008. Accessed July 30, 2016.
-
- Davis J. The Crypto-currency: Bitcoin and Its Mysterious Inventor. The New Yorker. http://www.newyorker.com/magazine/2011/10/10/the-crypto-currency. Accessed January 11, 2017.
-
- Calvery JS. Statement of Jennifer Shasky Calvery, Director Financial Crimes Enforcement Network United States Department of the Treasury. Vienna, Virginia, United States: Financial Crimes Enforcement Network; 2013.
-
- Dillet R. Bitcoin Ticker Available On Bloomberg Terminal For Employees. TechCrunch. https://techcrunch.com/2013/08/09/bitcoin-ticker-available-on-bloomberg-.... Accessed December 14, 2016.
-
- XE.COM INC. Currency Encyclopedia - XBT Bitcoin. http://www.xe.com/currency/xbt-bitcoin. Accessed February 15, 2017.

