A Cross-Layer, Anomaly-Based IDS for WSN and MANET
- PMID: 29470446
- PMCID: PMC5855147
- DOI: 10.3390/s18020651
A Cross-Layer, Anomaly-Based IDS for WSN and MANET
Abstract
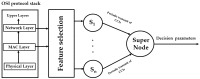
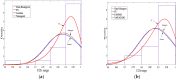
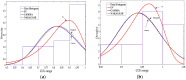
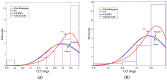
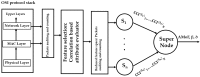
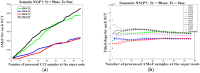
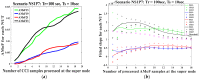
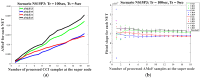
Intrusion detection system (IDS) design for mobile adhoc networks (MANET) is a crucial component for maintaining the integrity of the network. The need for rapid deployment of IDS capability with minimal data availability for training and testing is an important requirement of such systems, especially for MANETs deployed in highly dynamic scenarios, such as battlefields. This work proposes a two-level detection scheme for detecting malicious nodes in MANETs. The first level deploys dedicated sniffers working in promiscuous mode. Each sniffer utilizes a decision-tree-based classifier that generates quantities which we refer to as correctly classified instances (CCIs) every reporting time. In the second level, the CCIs are sent to an algorithmically run supernode that calculates quantities, which we refer to as the accumulated measure of fluctuation (AMoF) of the received CCIs for each node under test (NUT). A key concept that is used in this work is that the variability of the smaller size population which represents the number of malicious nodes in the network is greater than the variance of the larger size population which represents the number of normal nodes in the network. A linear regression process is then performed in parallel with the calculation of the AMoF for fitting purposes and to set a proper threshold based on the slope of the fitted lines. As a result, the malicious nodes are efficiently and effectively separated from the normal nodes. The proposed scheme is tested for various node velocities and power levels and shows promising detection performance even at low-power levels. The results presented also apply to wireless sensor networks (WSN) and represent a novel IDS scheme for such networks.
Keywords: MANET; WSN; accumulated measure of fluctuation (AMoF); decision trees; finite sample size; intrusion detection; linear regression.
Conflict of interest statement
The authors declare no conflict of interest.
Figures
References
-
- Raudys S.J., Jain A.K. Small Sample Size Effects in Statistical Pattern Recognition: Recommendations for Practitioners. IEEE Trans. Pattern Anal. Mach. Intell. 1991;13:252–264. doi: 10.1109/34.75512. - DOI
-
- Wang B., Zheng Y., Lou W., Hou Y.T. DDoS attack protection in the era of cloud computing and software-defined networking. Comput. Netw. 2015;81:308–319.
-
- Butun I., Morgera S.D., Sankar R. A survey of intrusion detection systems in wireless sensor networks. IEEE Commun. Surv. Tutor. 2014;16:266–282. doi: 10.1109/SURV.2013.050113.00191. - DOI
-
- Sinclair C., Pierce L., Matzner S. An application of machine learning to network intrusion detection; Proceedings of the 15th Annual Computer Security Applications Conference (ACSAC’99); Washington, DC, USA. 6–10 December 1999; pp. 371–377.
-
- Lee W., Stolfo S.J. A framework for constructing features and models for intrusion detection systems. ACM Trans. Inf. Syst. Secur. (TiSSEC) 2000;3:227–261. doi: 10.1145/382912.382914. - DOI
LinkOut - more resources
Full Text Sources
Other Literature Sources
Research Materials

