Dynamic Group Multi-party Quantum Key Agreement
- PMID: 29545516
- PMCID: PMC5854695
- DOI: 10.1038/s41598-018-21658-6
Dynamic Group Multi-party Quantum Key Agreement
Abstract
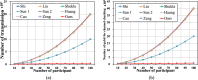
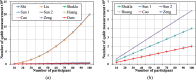
This paper presents a novel dynamic group multi-party Quantum Key Agreement (DGMQKA) protocol, achieved by a multicast transmission method. The proposed method is able to achieve arbitrary number of groups and members under the same resources. In addition, it can be dynamically adjusted by joining a new member, combining two groups into one group, revoking an old member and dividing one group into two groups, for different and complex situations. Furthermore, the proposed protocol can be of help to research into Quantum Secret Sharing (QSS), which it complements. The security analysis shows that the proposed protocol can resist both external and internal attacks. In consumption comparison, the proposed protocol using the multicast transmission method is more effective than other current MQKA protocols.
Conflict of interest statement
The authors declare no competing interests.
Figures


References
-
- Bennett, C. H. & Brassard, G. Quantum cryptography: Public key distribution and coin tossing. In in Proceedings of the IEEE International Conference on Computers, Systems, and Signal Processing, Bangalore, 175–179 (1984).
-
- Mayers D. Unconditional security in quantum cryptography. Journal of the ACM (JACM) 2001;48:351–406. doi: 10.1145/382780.382781. - DOI
LinkOut - more resources
Full Text Sources
Other Literature Sources

