Clone tag detection in distributed RFID systems
- PMID: 29565982
- PMCID: PMC5863942
- DOI: 10.1371/journal.pone.0193951
Clone tag detection in distributed RFID systems
Abstract
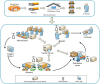
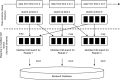
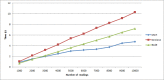
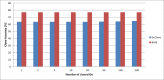
Although Radio Frequency Identification (RFID) is poised to displace barcodes, security vulnerabilities pose serious challenges for global adoption of the RFID technology. Specifically, RFID tags are prone to basic cloning and counterfeiting security attacks. A successful cloning of the RFID tags in many commercial applications can lead to many serious problems such as financial losses, brand damage, safety and health of the public. With many industries such as pharmaceutical and businesses deploying RFID technology with a variety of products, it is important to tackle RFID tag cloning problem and improve the resistance of the RFID systems. To this end, we propose an approach for detecting cloned RFID tags in RFID systems with high detection accuracy and minimal overhead thus overcoming practical challenges in existing approaches. The proposed approach is based on consistency of dual hash collisions and modified count-min sketch vector. We evaluated the proposed approach through extensive experiments and compared it with existing baseline approaches in terms of execution time and detection accuracy under varying RFID tag cloning ratio. The results of the experiments show that the proposed approach outperforms the baseline approaches in cloned RFID tag detection accuracy.
Conflict of interest statement
Figures



Similar articles
-
ACD: An Adaptable Approach for RFID Cloning Attack Detection.Sensors (Basel). 2020 Apr 22;20(8):2378. doi: 10.3390/s20082378. Sensors (Basel). 2020. PMID: 32331407 Free PMC article.
-
A hash based mutual RFID tag authentication protocol in telecare medicine information system.J Med Syst. 2015 Jan;39(1):153. doi: 10.1007/s10916-014-0153-7. Epub 2014 Dec 10. J Med Syst. 2015. PMID: 25491577
-
A Secure ECC-based RFID Mutual Authentication Protocol to Enhance Patient Medication Safety.J Med Syst. 2016 Jan;40(1):12. doi: 10.1007/s10916-015-0362-8. Epub 2015 Oct 29. J Med Syst. 2016. PMID: 26573649
-
Overview of RFID technology and its applications in the food industry.J Food Sci. 2009 Oct;74(8):R101-6. doi: 10.1111/j.1750-3841.2009.01323.x. J Food Sci. 2009. PMID: 19799677 Review.
-
Survey: Vulnerability Analysis of Low-Cost ECC-Based RFID Protocols against Wireless and Side-Channel Attacks.Sensors (Basel). 2021 Aug 30;21(17):5824. doi: 10.3390/s21175824. Sensors (Basel). 2021. PMID: 34502714 Free PMC article. Review.
Cited by
-
ACD: An Adaptable Approach for RFID Cloning Attack Detection.Sensors (Basel). 2020 Apr 22;20(8):2378. doi: 10.3390/s20082378. Sensors (Basel). 2020. PMID: 32331407 Free PMC article.
References
-
- J. Abawajy, “Enhancing RFID tag resistance against cloning attack,” in Network and System Security, 2009. NSS’09. Third International Conference on, 2009, pp. 18–23.
-
- Huang Y., Xu Y., Qi S., Fang X., and Yin X., “Recent Patents on RFID-Based Logistics Management Systems,” Recent Patents Mech. Eng., vol. 9, no. 1, pp. 26–36, 2016.
-
- Mahdin H., Kamaludin H., Saedudin R. D. R., Omar A. H., Kasim S., and Jailani J., “The Application of RFID System in Water Level Monitoring,” Int. J. Adv. Sci. Eng. Inf. Technol., vol. 7, no. 4–2, pp. 1522–1527, 2017.
-
- N. Alzahrani and N. Bulusu, “Securing Pharmaceutical and High-Value Products against Tag Reapplication Attacks Using NFC Tags,” in Smart Computing (SMARTCOMP), 2016 IEEE International Conference on, 2016, pp. 1–6.
Publication types
MeSH terms
LinkOut - more resources
Full Text Sources
Other Literature Sources

