Statistical Models for Predicting Threat Detection From Human Behavior
- PMID: 29713296
- PMCID: PMC5911499
- DOI: 10.3389/fpsyg.2018.00466
Statistical Models for Predicting Threat Detection From Human Behavior
Abstract
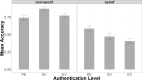
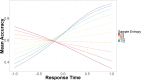
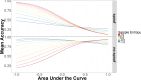
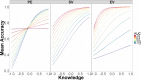
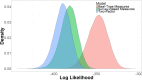
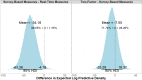
Users must regularly distinguish between secure and insecure cyber platforms in order to preserve their privacy and safety. Mouse tracking is an accessible, high-resolution measure that can be leveraged to understand the dynamics of perception, categorization, and decision-making in threat detection. Researchers have begun to utilize measures like mouse tracking in cyber security research, including in the study of risky online behavior. However, it remains an empirical question to what extent real-time information about user behavior is predictive of user outcomes and demonstrates added value compared to traditional self-report questionnaires. Participants navigated through six simulated websites, which resembled either secure "non-spoof" or insecure "spoof" versions of popular websites. Websites also varied in terms of authentication level (i.e., extended validation, standard validation, or partial encryption). Spoof websites had modified Uniform Resource Locator (URL) and authentication level. Participants chose to "login" to or "back" out of each website based on perceived website security. Mouse tracking information was recorded throughout the task, along with task performance. After completing the website identification task, participants completed a questionnaire assessing their security knowledge and degree of familiarity with the websites simulated during the experiment. Despite being primed to the possibility of website phishing attacks, participants generally showed a bias for logging in to websites versus backing out of potentially dangerous sites. Along these lines, participant ability to identify spoof websites was around the level of chance. Hierarchical Bayesian logistic models were used to compare the accuracy of two-factor (i.e., website security and encryption level), survey-based (i.e., security knowledge and website familiarity), and real-time measures (i.e., mouse tracking) in predicting risky online behavior during phishing attacks. Participant accuracy in identifying spoof and non-spoof websites was best captured using a model that included real-time indicators of decision-making behavior, as compared to two-factor and survey-based models. Findings validate three widely applicable measures of user behavior derived from mouse tracking recordings, which can be utilized in cyber security and user intervention research. Survey data alone are not as strong at predicting risky Internet behavior as models that incorporate real-time measures of user behavior, such as mouse tracking.
Keywords: cyber security; cyberpsychology; human dynamics; mouse tracking; phishing; statistical models; threat detection.
Figures



Similar articles
-
Detecting phishing websites using machine learning technique.PLoS One. 2021 Oct 11;16(10):e0258361. doi: 10.1371/journal.pone.0258361. eCollection 2021. PLoS One. 2021. Retraction in: PLoS One. 2025 Apr 23;20(4):e0322065. doi: 10.1371/journal.pone.0322065. PMID: 34634081 Free PMC article. Retracted.
-
Susceptibility and resilience to cyber threat: Findings from a scenario decision program to measure secure and insecure computing behavior.PLoS One. 2018 Dec 12;13(12):e0207408. doi: 10.1371/journal.pone.0207408. eCollection 2018. PLoS One. 2018. PMID: 30540758 Free PMC article.
-
A comprehensive survey of AI-enabled phishing attacks detection techniques.Telecommun Syst. 2021;76(1):139-154. doi: 10.1007/s11235-020-00733-2. Epub 2020 Oct 23. Telecommun Syst. 2021. PMID: 33110340 Free PMC article. Review.
-
Cyber Threat Intelligence-Based Malicious URL Detection Model Using Ensemble Learning.Sensors (Basel). 2022 Apr 28;22(9):3373. doi: 10.3390/s22093373. Sensors (Basel). 2022. PMID: 35591061 Free PMC article.
-
The Role of User Behaviour in Improving Cyber Security Management.Front Psychol. 2021 Jun 18;12:561011. doi: 10.3389/fpsyg.2021.561011. eCollection 2021. Front Psychol. 2021. PMID: 34220596 Free PMC article. Review.
Cited by
-
Can You Hear Me Now? Audio and Visual Interactions That Change App Choices.Front Psychol. 2020 Oct 15;11:2227. doi: 10.3389/fpsyg.2020.02227. eCollection 2020. Front Psychol. 2020. PMID: 33178056 Free PMC article.
References
-
- Ablon L., Libicki M. C., Golay A. A. (2014). Markets for Cybercrime Tools and Stolen Data. Santa Monica, CA: National Security Research Division, 1–85. 10.7249/j.ctt6wq7z6 - DOI
-
- Almuhimedi H., Felt A. P., Reeder R. W., Consolvo S. (2014). “Your reputation precedes you: history, reputation, and the chrome malware warning,” in SOUPS ’14: Proceedings of the Tenth Symposium on Usable Privacy and Security, Menlo Park, CA, 113–128.
-
- Alsharnouby M., Alaca F., Chiasson S. (2015). Why phishing still works: user strategies for combating phishing attacks. Int. J. Hum. Comput. Stud. 82 69–82. 10.1016/j.ijhcs.2015.05.005 - DOI
-
- Anti-Phishing Working Group [APWG] (2016). Phishing Activity Trends Report Q4 2016. APWG, (December 2016), 14. Available at: http://docs.apwg.org/reports/apwg_trends_report_q4_2016.pdf
-
- Arianezhad M., Camp L. J., Kelley T., Stebila D. (2013). “Comparative eye tracking of experts and novices in web single sign-on,” in Proceedings of the Third ACM Conference on Data and Application Security and Privacy - CODASPY ’13 (New York, NY: ACM Press; ), 105 10.1145/2435349.2435362 - DOI
LinkOut - more resources
Full Text Sources
Other Literature Sources