Comparison and Feasibility of Various RFID Authentication Methods Using ECC
- PMID: 30200493
- PMCID: PMC6164036
- DOI: 10.3390/s18092902
Comparison and Feasibility of Various RFID Authentication Methods Using ECC
Abstract
Radio frequency identification (RFID) is a technology that has grown in popularity and in the applications of use. However, there are major issues regarding security and privacy with respect to RFID technology which have caught the interest of many researchers. There are significant challenges which must be overcome to resolve RFID security and privacy issues. One reason is the constraints attached to the provision of security and privacy in RFID systems. Along with meeting the security and privacy needs of RFID technology, solutions must be inexpensive, practical, reliable, scalable, flexible, inter-organizational, and long-lasting. To make RFID identifiers effective and efficient they must identify the item(s) while resisting attacks aimed at obtaining the tag's information and compromising the system or making it possible to bypass the protection RFID tags are supposed to provide. Different authentication methods have been proposed, researched, and evaluated in the literature. In this work, we proposed our methodology in evaluating RFID authentication, and a few of the most promising authentication methods are reviewed, compared, and ranked in order to arrive at a possible best choice of protocol to use.
Keywords: IoT; RFID; Random Access Control; authentication; elliptic curve cryptography; lightweight protocol; privacy; security.
Conflict of interest statement
The authors declare no conflicts of interest.
Figures
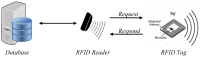







References
-
- Gope P., Hwang T. A realistic lightweight authentication protocol preserving strong anonymity for securing RFID system. Comput. Secur. 2015;55:271–280. doi: 10.1016/j.cose.2015.05.004. - DOI
-
- Gope P., Lee J., Quek T.Q.S. Lightweight and Practical Anonymous Authentication Protocol for RFID Systems Using Physically Unclonable Functions. IEEE Trans. Inf. Forensics Secur. 2018;13:2831–2843. doi: 10.1109/TIFS.2018.2832849. - DOI
-
- Alamr A.A., Kausar F., Kim J.S. Secure mutual authentication protocol for RFID based on elliptic curve cryptography; Proceedings of the 2016 International Conference on Platform Technology and Service (PlatCon); Jeju, Korea. 15–17 February 2016; pp. 1–7.
-
- Zheng L., Xue Y., Zhang L., Zhang R. Mutual Authentication Protocol for RFID based on ECC; Proceedings of the IEEE International Conference on Computational Science and Engineering (CSE) and IEEE International Conference on Embedded and Ubiquitous Computing (EUC); Guangzhou, China. 21–24 July 2017; pp. 320–323.
Publication types
LinkOut - more resources
Full Text Sources
Other Literature Sources
Molecular Biology Databases

