The state of research on cyberattacks against hospitals and available best practice recommendations: a scoping review
- PMID: 30634962
- PMCID: PMC6330387
- DOI: 10.1186/s12911-018-0724-5
The state of research on cyberattacks against hospitals and available best practice recommendations: a scoping review
Abstract
Background: The health sector has quickly become a target for cyberattacks. Hospitals are especially sensitive to these sorts of attacks as any disruption in operations or even disclosure of patient personal information can have far-reaching consequences. The objective of this study was to map the available literature on cyberattacks on hospitals and to identify the different domains of research, while extracting the recommendations and guidelines put forth in the literature.
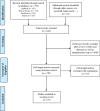
Methods: Four databases (PubMed, Web of Science, ProQuest, and Scopus) were searched using standardized and adapted search syntax in order to identify relevant manuscripts published between 1997 and 2017. These were screened by two reviewers and included or excluded based on inclusion and exclusion criteria. Data from articles were then extracted and analyzed.
Results: The search identified 818 records of which 97 were included. Of the 97, 32% were published in 2017 while around 40% of the articles were published prior to the last three years. Six domains of research emerged through the analysis, which are included here: context and trends in cybersecurity (27.8%), connected medical devices and equipment (29.9%), hospital information systems (14.4%), raising awareness and lessons learned (6.2%), information security methodology (15.4%), and specific types of attacks (6.2%).
Conclusion: There is a generally growing interest in the research field, but the available literature remains limited in number. There are important aspects of cybersecurity (e.g. cloud storage and access management) as well as specific medical fields that rely on various medical devices that have been neglected. Recommendations are available, but comprehensive guidelines and standardized best practice measures are still necessary.
Keywords: Cyberattacks; Cybersecurity recommendations; Hospital cybersecurity; Medical device security.
Conflict of interest statement
Ethics approval and consent to participate
Not applicable
Consent for publication
Not applicable
Competing interests
The authors declare that they have no competing interests.
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Figures
References
-
- Health Care in Danger: Making the Case. Geneva: International Committee of the Red Cross; 2011. 4–22.
-
- Long S. The cyber attack - from the POV of the CEO - Hancock regional hospital. Hancock Health 2018. https://www.hancockregionalhospital.org/2018/01/cyber-attack-pov-ceo/. Accessed 21 Feb 2018.
-
- Bisson D. Hollywood hospital pays $17,000 to ransomware attackers. The State of Security 2016. https://www.tripwire.com/state-of-security/latest-security-news/hollywoo.... Accessed 20 Feb 2018.
-
- Hughes O. Norway healthcare cyber-attack could be biggest of its kind. Digital Health. 2018; https://www.digitalhealth.net/2018/01/norway-healthcare-cyber-attack-cou.... Accessed 21 Feb 2018.
-
- Muchai C, Kimani K, Mwangi M, Shiyayo B, Ndegwa D, Kaimba B, et al. Kenya Cyber Security Report 2015. Nairobi, Kenya: Serianu; 2015. 8–45.
Publication types
MeSH terms
LinkOut - more resources
Full Text Sources
Medical