Enabling the Deployment of ABAC Policies in RBAC Systems
- PMID: 30687849
- PMCID: PMC6345267
- DOI: 10.1007/978-3-319-95729-6_4
Enabling the Deployment of ABAC Policies in RBAC Systems
Abstract
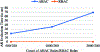
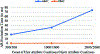
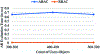
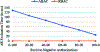
The flexibility, portability and identity-less access control features of Attribute Based Access Control (ABAC) make it an attractive choice to be employed in many application domains. However, commercially viable methods for implementation of ABAC do not exist while a vast majority of organizations use Role Based Access Control (RBAC) systems. In this paper, we present a way in which organizations having a RBAC system can deploy an ABAC policy. Thus, we propose a method for the translation of an ABAC policy into a form that can be adopted by an RBAC system. We compare the cost of enforcement in ABAC and RBAC with respect to time taken to evaluate an access request, and experimentally demonstrate that RBAC is significantly better in this respect. Since the cost of security management is more expensive under RBAC when compared to ABAC, we present an analysis of the different management costs and present mitigation approaches by considering various administrative operations.
Figures
References
-
- Hu VC, Ferraiolo D, Kuhn R, Schnitzer A, Sandlin K, Miller R, Scarfone K: Guide to Attribute Based Access Control (ABAC) definition and considerations. In: NIST Special Publication, 800–162 (2014)
-
- Jha S, Sural S, Atluri V, Vaidya J: Enforcing separation of duty in attribute based access control systems. In: ICISS, pp. 61–78 (2015)
-
- Uzun E, Lorenzi D, Atluri V, Vaidya J, Sural S: Migrating from DAC to RBAC. In: DBSec, pp. 69–84 (2015)
-
- Vaidya J, Atluri V, Guo Q: The role mining problem: finding a minimal descriptive set of roles. In: SACMAT, pp. 175–184 (2007)
-
- Huang J, Nicol D, Bobba R, Huh J: A framework integrating attribute-based policies into role-based access control. In: SACMAT, pp. 187–196 (2012)
Grants and funding
LinkOut - more resources
Full Text Sources
Other Literature Sources