Data mining for mutation-specific targets in acute myeloid leukemia
- PMID: 30728456
- PMCID: PMC7250137
- DOI: 10.1038/s41375-019-0387-y
Data mining for mutation-specific targets in acute myeloid leukemia
Abstract
Three mutation-specific targeted therapies have recently been approved by the FDA for the treatment of acute myeloid leukemia (AML): midostaurin for FLT3 mutations, enasidenib for relapsed or refractory cases with IDH2 mutations, and ivosidenib for cases with an IDH1 mutation. Together, these agents offer a mutation-directed treatment approach for up to 45% of de novo adult AML cases, a welcome deluge after a prolonged drought. At the same time, a number of computational tools have recently been developed that promise to further accelerate progress in mutation-specific therapy for AML and other cancers. Technical advances together with comprehensively annotated AML tissue banks have resulted in the availability of large and complex data sets for exploration by the end-user, including (i) microarray gene expression, (ii) exome sequencing, (iii) deep sequencing data of sub-clone heterogeneity, (iv) RNA sequencing of gene expression (bulk and single cell), (v) DNA methylation and chromatin, (vi) and germline quantitative trait loci. Yet few clinicians or experimental hematologists have the time or the training to access or analyze these repositories. This review summarizes the data sets and bioinformatic tools currently available to further the discovery of mutation-specific targets with an emphasis on web-based applications that are open, accessible, user-friendly, and do not require coding experience to navigate. We show examples of how available data can be mined to identify potential targets using synthetic lethality, drug repurposing, epigenetic sub-grouping, and proteomic networks while also highlighting strengths and limitations and the need for superior models for validation.
Conflict of interest statement
Conflict of Interest:
The authors declare no conflict of interest.
Figures
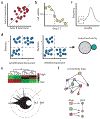
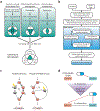
References
-
- Valk PJM, Verhaak RGW, Beijen MA, Erpelinck CAJ, van Doorn-Khosrovani SB van W, Boer JM et al. Prognostically Useful Gene-Expression Profiles in Acute Myeloid Leukemia. N Engl J Med 2004; 350: 1617–1628. - PubMed
Publication types
MeSH terms
Substances
Grants and funding
LinkOut - more resources
Full Text Sources
Medical
Miscellaneous

