Are Market GM Plants an Unrecognized Platform for Bioterrorism and Biocrime?
- PMID: 31192204
- PMCID: PMC6549539
- DOI: 10.3389/fbioe.2019.00121
Are Market GM Plants an Unrecognized Platform for Bioterrorism and Biocrime?
Abstract
This article discusses a previously unrecognized avenue for bioterrorism and biocrime. It is suggested that new gene editing technologies may have the potential to create plants that are genetically modified in harmful ways, either in terms of their effect on the plant itself or in terms of harming those who would consume foods produced by that plant. While several risk scenarios involving GMOs-such as antibiotic resistant pathogens, synthetic biology, or mixing of non-GMO seeds with GMO seeds-have previously have been recognized, the new vulnerability is rooted in a different paradigm-that of clandestinely manipulating GMOs to create damage. The ability to actively inflict diseases on plants would pose serious health hazards to both humans and animals, have detrimental consequences to the economy, and directly threaten the food supply. As this is the first study of this kind, the full scope and impact of suck attacks-especially those involving the intended misuse of technologies such as gene-drives-merits further investigation. Herein, the plausibility of some of the new risks will be analyzed by, (1) Highlighting ownership and origination issues (esp. of event-specific GM-plants) as unrecognized risk factors; (2) Investigating the unique role of GMOs, why-and how-certified GMOs could become a new venue for such attacks; (3) Analyzing possible dual-use potentials of modern technologies and research oriented toward the advancement of GMOs, plant breeding and crop improvement. The identification and analysis of harmful genetic manipulations to utilize (covertly modified) plants (GMOs and non-GMOs) as an attack vector show that these concerns need to be taken seriously, raising the prospect not only of direct harm, but of the more likely effects in generating public concern, reputational harm of agricultural biotechnology companies, law-suits, and increased import bans of certain plants or their derived products.
Keywords: GMO authentication; GMO counterfeiting; clandestine manipulation of biological mediums; covert manipulation of non-GMOs; plants as attack vectors; unauthorized GMOs; unrecognized bio-weapons.
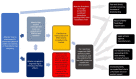
Figures


Similar articles
-
EFSA's scientific activities and achievements on the risk assessment of genetically modified organisms (GMOs) during its first decade of existence: looking back and ahead.Transgenic Res. 2014 Feb;23(1):1-25. doi: 10.1007/s11248-013-9741-4. Epub 2013 Aug 21. Transgenic Res. 2014. PMID: 23963741 Review.
-
Approaches in the risk assessment of genetically modified foods by the Hellenic Food Safety Authority.Food Chem Toxicol. 2007 Apr;45(4):530-42. doi: 10.1016/j.fct.2006.07.009. Epub 2006 Aug 25. Food Chem Toxicol. 2007. PMID: 17275157 Review.
-
Genetically modified seeds and plant propagating material in Europe: potential routes of entrance and current status.Heliyon. 2019 Feb 15;5(2):e01242. doi: 10.1016/j.heliyon.2019.e01242. eCollection 2019 Feb. Heliyon. 2019. PMID: 30815609 Free PMC article. Review.
-
Need for an "integrated safety assessment" of GMOs, linking food safety and environmental considerations.J Agric Food Chem. 2006 May 3;54(9):3173-80. doi: 10.1021/jf0511650. J Agric Food Chem. 2006. PMID: 16637668
-
See what you eat--broad GMO screening with microarrays.Anal Bioanal Chem. 2010 Mar;396(6):1961-7. doi: 10.1007/s00216-009-3204-z. Epub 2009 Oct 28. Anal Bioanal Chem. 2010. PMID: 19862507
Cited by
-
High-Throughput Shotgun Metagenomics of Microbial Footprints Uncovers a Cocktail of Noxious Antibiotic Resistance Genes in the Winam Gulf of Lake Victoria, Kenya.J Trop Med. 2024 Dec 23;2024:7857069. doi: 10.1155/jotm/7857069. eCollection 2024. J Trop Med. 2024. PMID: 39741524 Free PMC article.
-
The worsening divergence of biotechnology: the importance of risk culture.Front Bioeng Biotechnol. 2023 Aug 30;11:1250298. doi: 10.3389/fbioe.2023.1250298. eCollection 2023. Front Bioeng Biotechnol. 2023. PMID: 37711457 Free PMC article.
-
GMOs or non-GMOs? The CRISPR Conundrum.Front Plant Sci. 2023 Oct 9;14:1232938. doi: 10.3389/fpls.2023.1232938. eCollection 2023. Front Plant Sci. 2023. PMID: 37877083 Free PMC article. Review.
-
Genetic Information Insecurity as State of the Art.Front Bioeng Biotechnol. 2020 Dec 8;8:591980. doi: 10.3389/fbioe.2020.591980. eCollection 2020. Front Bioeng Biotechnol. 2020. PMID: 33381496 Free PMC article.
-
Facing the 2020 pandemic: What does cyberbiosecurity want us to know to safeguard the future?Biosaf Health. 2021 Feb;3(1):11-21. doi: 10.1016/j.bsheal.2020.09.007. Epub 2020 Sep 25. Biosaf Health. 2021. PMID: 33015604 Free PMC article. Review.
References
-
- Adang M. J., Crickmore N., Jurat-Fuentes J. L. (2014). Diversity of Bacillus thuringiensis crystal toxins and mechanism of action, in Advances in Insect Physiology, eds Dhadialla T. S., Gill (Elsevier) S. S. 47, 39–87.
-
- Anderson R. J. (2010). Security Engineering: A Guide to Building Dependable Distributed Systems, Indianapolis, IN: John Wiley & Sons.
LinkOut - more resources
Full Text Sources
Research Materials