A Cancelable Iris- and Steganography-Based User Authentication System for the Internet of Things
- PMID: 31284592
- PMCID: PMC6651016
- DOI: 10.3390/s19132985
A Cancelable Iris- and Steganography-Based User Authentication System for the Internet of Things
Abstract
Remote user authentication for Internet of Things (IoT) devices is critical to IoT security, as it helps prevent unauthorized access to IoT networks. Biometrics is an appealing authentication technique due to its advantages over traditional password-based authentication. However, the protection of biometric data itself is also important, as original biometric data cannot be replaced or reissued if compromised. In this paper, we propose a cancelable iris- and steganography-based user authentication system to provide user authentication and secure the original iris data. Most of the existing cancelable iris biometric systems need a user-specific key to guide feature transformation, e.g., permutation or random projection, which is also known as key-dependent transformation. One issue associated with key-dependent transformations is that if the user-specific key is compromised, some useful information can be leaked and exploited by adversaries to restore the original iris feature data. To mitigate this risk, the proposed scheme enhances system security by integrating an effective information-hiding technique-steganography. By concealing the user-specific key, the threat of key exposure-related attacks, e.g., attacks via record multiplicity, can be defused, thus heightening the overall system security and complementing the protection offered by cancelable biometric techniques.
Keywords: cancelable; feature data protection; iris; steganography.
Conflict of interest statement
The authors declare no conflict of interest.
Figures
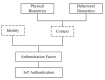
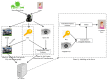
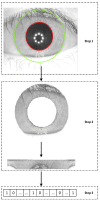
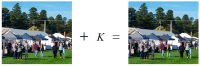

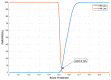
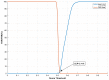
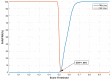
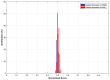
References
-
- Ashton K. That ‘internet of things’ thing. RFID J. 2009;22:97–114.
-
- Habib K., Torjusen A., Leister W. A novel authentication framework based on biometric and radio fingerprinting for the IoT in eHealth; Proceedings of the 2014 International Conference on Smart Systems, Devices and Technologies (SMART); Paris, France. 20–24 July 2014; pp. 32–37.
-
- Macedo M.J., Yang W., Zheng G., Johnstone M.N. A comparison of 2D and 3D Delaunay triangulations for fingerprint authentication; Proceedings of the 2017 Australian Information Security Management Conference; Perth, Australia. 5–6 December 2017; pp. 108–115.
-
- Lai Y.-L., Jin Z., Teoh A.B.J., Goi B.-M., Yap W.-S., Chai T.-Y., Rathgeb C. Cancellable iris template generation based on Indexing-First-One hashing. Pattern Recognit. 2017;64:105–117.
-
- Masek L. Iris Recognition. [(accessed on 19 April 2019)]; Available online: https://www.peterkovesi.com/studentprojects/libor/
LinkOut - more resources
Full Text Sources
Other Literature Sources

