Monitoring hyperproperties
- PMID: 31806925
- PMCID: PMC6853877
- DOI: 10.1007/s10703-019-00334-z
Monitoring hyperproperties
Abstract
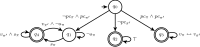
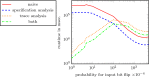
Hyperproperties, such as non-interference and observational determinism, relate multiple system executions to each other. They are not expressible in standard temporal logics, like LTL, CTL, and CTL*, and thus cannot be monitored with standard runtime verification techniques. extends linear-time temporal logic (LTL) with explicit quantification over traces in order to express hyperproperties. We investigate the runtime verification problem of formulas for three different input models: (1) The parallel model, where a fixed number of system executions is processed in parallel. (2) The unbounded sequential model, where system executions are processed sequentially, one execution at a time. In this model, the number of incoming executions is a-priori unbounded and may in fact grow forever. (3) The bounded sequential model where the traces are processed sequentially and the number of incoming executions is bounded. We show that the existence of a bound in the parallel and bounded sequential models leads to a different notion of monitorability than in the unbounded sequential model. We show that deciding the monitoriability problem for alternation-free HyperLTL is -complete while the problem is undecidable in general. For every input model, we provide monitoring algorithms along with run-time and storage optimizations. By recognizing properties of specifications such as reflexivity, symmetry, and transitivity, we reduce the number of comparisons between traces. For the sequential models, we present a technique that minimizes the number of traces that need to be stored. We evaluate our optimizations, showing that this leads to a more scalable monitoring and, in particular, a significantly lower memory consumption.
Keywords: Hyperproperties; Information-flow; Monitoring; Runtime verification.
© The Author(s) 2019.
Figures









References
-
- Agrawal S, Bonakdarpour B (2016) Runtime verification of k-safety hyperproperties in HyperLTL. In: Proceedings of CSF, IEEE Computer Society, pp 239–252
-
- Askarov A, Sabelfeld A (2009) Tight enforcement of information-release policies for dynamic languages. In: Proceedings of CSF, IEEE Computer Society, pp 43–59
-
- Austin TH, Flanagan C (2010) Permissive dynamic information flow analysis. In: Proceedings of PLAS, ACM, p 3
-
- Barringer H, Falcone Y, Havelund K, Reger G, Rydeheard DE (2012) Quantified event automata: towards expressive and efficient runtime monitors. In: Proceedings of FM, volume 7436 of LNCS, Springer, pp 68–84
-
- Bauer A (2010) Monitorability of omega-regular languages. In: CoRR. arXiv:1006.3638
LinkOut - more resources
Full Text Sources
