A Machine Learning Based Intrusion Detection System for Mobile Internet of Things
- PMID: 31947567
- PMCID: PMC7013568
- DOI: 10.3390/s20020461
A Machine Learning Based Intrusion Detection System for Mobile Internet of Things
Abstract
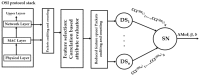
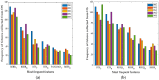
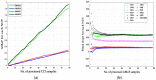
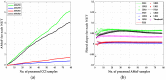
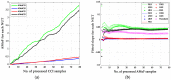
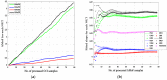
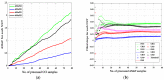
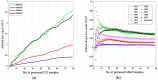
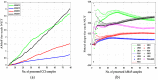
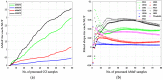
Intrusion detection systems plays a pivotal role in detecting malicious activities that denigrate the performance of the network. Mobile adhoc networks (MANETs) and wireless sensor networks (WSNs) are a form of wireless network that can transfer data without any need of infrastructure for their operation. A more novel paradigm of networking, namely Internet of Things (IoT) has emerged recently which can be considered as a superset to the afore mentioned paradigms. Their distributed nature and the limited resources available, present a considerable challenge for providing security to these networks. The need for an intrusion detection system (IDS) that can acclimate with such challenges is of extreme significance. Previously, we proposed a cross layer-based IDS with two layers of detection. It uses a heuristic approach which is based on the variability of the correctly classified instances (CCIs), which we refer to as the accumulated measure of fluctuation (AMoF). The current, proposed IDS is composed of two stages; stage one collects data through dedicated sniffers (DSs) and generates the CCI which is sent in a periodic fashion to the super node (SN), and in stage two the SN performs the linear regression process for the collected CCIs from different DSs in order to differentiate the benign from the malicious nodes. In this work, the detection characterization is presented for different extreme scenarios in the network, pertaining to the power level and node velocity for two different mobility models: Random way point (RWP), and Gauss Markov (GM). Malicious activity used in the work are the blackhole and the distributed denial of service (DDoS) attacks. Detection rates are in excess of 98% for high power/node velocity scenarios while they drop to around 90% for low power/node velocity scenarios.
Keywords: AMoF; IoT; WSN; intrusion detection systems; linear regression; random forest.
Conflict of interest statement
The authors declare no conflict of interest.
Figures
References
-
- Mishra A., Sudan K., Soliman H. Detecting Border Intrusion Using Wireless Sensor Network and Artificial Neural Network; Proceedings of the 6th IEEE international conference on distributed computing in sensor systems workshops (DCOSSW); Santa Barbara, CA, USA. 21–23 June 2010; pp. 1–6.
-
- Diro A.A., Chilamkurti N. Distributed Attack Detection Scheme Using Deep Learning Approach for Internet of Things. Future Gener. Comput. Syst. 2018;82:761–768. doi: 10.1016/j.future.2017.08.043. - DOI
-
- Kaplantzis S., Shilton A., Nallasamy M., Sekercioglu Y. Detecting Selective Forwarding Attacks in Wireless Sensor Networks Using Support Vector Machines; Proceedings of the 3rd IEEE International Conference on Intelligent Sensors, Sensor Networks and Information; Melbourne, Australia. 3–6 December 2007; pp. 335–340.
-
- Amouri A., Jaimes L.G., Manthena R., Morgera S.D., Vergara-Laurens I.J. A simple scheme for pseudo clustering algorithm for cross layer intrusion detection in MANET; Proceedings of the 7th IEEE Latin-American Conference on Communications (LATINCOM); Arequipa, Peru. 4–6 November 2015; pp. 1–6.
-
- Sutharshan R., Leckie C., Palaniswami M., Bezdek J.C. Anomaly Detection in Wireless Sensor Networks. IEEE Wirel. Commun. 2008;15:34–40.
LinkOut - more resources
Full Text Sources

