Optimal memory-aware backpropagation of deep join networks
- PMID: 31955681
- PMCID: PMC7015292
- DOI: 10.1098/rsta.2019.0049
Optimal memory-aware backpropagation of deep join networks
Abstract
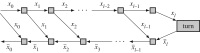
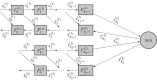
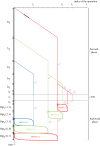
Deep learning training memory needs can prevent the user from considering large models and large batch sizes. In this work, we propose to use techniques from memory-aware scheduling and automatic differentiation (AD) to execute a backpropagation graph with a bounded memory requirement at the cost of extra recomputations. The case of a single homogeneous chain, i.e. the case of a network whose stages are all identical and form a chain, is well understood and optimal solutions have been proposed in the AD literature. The networks encountered in practice in the context of deep learning are much more diverse, both in terms of shape and heterogeneity. In this work, we define the class of backpropagation graphs, and extend those on which one can compute in polynomial time a solution that minimizes the total number of recomputations. In particular, we consider join graphs which correspond to models such as siamese or cross-modal networks. This article is part of a discussion meeting issue 'Numerical algorithms for high-performance computational science'.
Keywords: backpropagation; memory; pebble game.
Conflict of interest statement
We declare we have no competing interests.
Figures





References
-
- Glorot X, Bengio Y. 2010. Understanding the difficulty of training deep feedforward neural networks. In Proc. of the thirteenth Int. Conf. on Artificial Intelligence and Statistics, pp. 249–256.
-
- Dean J.et al.2012Large scale distributed deep networks. In Advances in neural information processing systems, pp. 1223–1231. (https://papers.nips.cc/paper/4687-large-scale-distributed-deep-networks)
-
- Das D, Avancha S, Mudigere D, Vaidynathan K, Sridharan S, Kalamkar D, Kaul B, Dubey P. 2016 Distributed deep learning using synchronous stochastic gradient descent. (http://arxiv.org/abs/1602.06709. )
-
- Sethi R. 1975. Complete register allocation problems. SIAM J. Comput. 4, 226–248. (10.1137/0204020) - DOI
-
- Liu JWH. 1987. An application of generalized tree pebbling to sparse matrix factorization. SIAM J. Algebr. Discret. Methods 8, 375–395. (10.1137/0608031) - DOI
MeSH terms
LinkOut - more resources
Full Text Sources