A Secure Enhanced Non-Cooperative Cognitive Division Multiple Access for Vehicle-to-Vehicle Communication
- PMID: 32069860
- PMCID: PMC7070490
- DOI: 10.3390/s20041000
A Secure Enhanced Non-Cooperative Cognitive Division Multiple Access for Vehicle-to-Vehicle Communication
Abstract
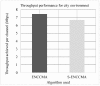
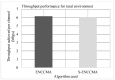
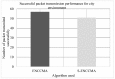
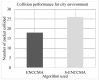
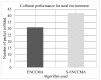
The growth of the Internet has led to the increasing usage of smart infotainment applications on the vehicular ad-hoc network (VANET). Preserving privacy and security regarding the provision of smart infotainment applications while on the go is most desired. Thus, a secure authentication scheme is required. Many privacy-preserving security schemes have been developed in recent times using cryptography approaches. However, these incur key management and communication overhead. The usage of third-party servers incurs the overhead of key computation, storage and distribution. Post completion of the initialization phase, the message is secured using cryptography and is shared among vehicles. The design of the proposed secure enhanced non-cooperative cognitive division multiple access ( S - ENCCMA ) aims to eliminate the need for the local message available with the parties to be released for provisioning secure safety-related applications. To overcome the research challenges, this work presents a novel security scheme, namely secure non-cooperative cognitive medium access ( S - ENCCMA ). The experiment is conducted to evaluate the overhead incurred in provisioning security to ENCCMA . The outcome shows that the overhead incurred by S - ENCCMA over ENCCMA was negligible to provide the real-time security requirements of smart infotainment applications, which is experimentally shown in this paper in terms of throughput, collision and successful packet transmission considering varied environmental models such as cities, highways and rural areas.
Keywords: MAC; line of sight; radio propagation; vanet; vehicle-to-vehicle.
Conflict of interest statement
The authors declare no conflict of interest.
Figures





References
-
- Ros F.J., Ruiz P.M., Stojmenovic I. Acknowledgment-based broadcast protocol for reliable and efficient data dissemination in vehicular ad hoc networks. IEEE Trans. Mob. Comput. 2012;11:33–46. doi: 10.1109/TMC.2010.253. - DOI
-
- Azees M., Vijayakumar P., Deborah L.J. Comprehensive survey on security services in vehicular ad-hoc networks. IET Intell. Transp. Syst. 2016;10:379–388. doi: 10.1049/iet-its.2015.0072. - DOI
-
- DSRC Technology, Intelligent Transportation Systems. [(accessed on 28 January 2011)]; Available online: http://www.its.dot.gov/dsrc/
-
- Parno B., Perrig A. Workshop on Hot Topics in Networks (HotNets-IV) University of Maryland; College Park, MD, USA: 2005. Challenges in securing vehicular networks; pp. 1–6.
-
- Raya M., Hubaux J.P. Securing vehicular ad hoc networks. J. Comput. Secur. 2007;15:39–68. doi: 10.3233/JCS-2007-15103. - DOI
Grants and funding
LinkOut - more resources
Full Text Sources

