Peer-to-Peer Contact Tracing: Development of a Privacy-Preserving Smartphone App
- PMID: 32240973
- PMCID: PMC7144575
- DOI: 10.2196/18936
Peer-to-Peer Contact Tracing: Development of a Privacy-Preserving Smartphone App
Abstract
Background: The novel coronavirus disease 2019 (COVID-19) pandemic is an urgent public health crisis, with epidemiologic models predicting severe consequences, including high death rates, if the virus is permitted to run its course without any intervention or response. Contact tracing using smartphone technology is a powerful tool that may be employed to limit disease transmission during an epidemic or pandemic; yet, contact tracing apps present significant privacy concerns regarding the collection of personal data such as location.
Objective: The aim of this study is to develop an effective contact tracing smartphone app that respects user privacy by not collecting location information or other personal data.
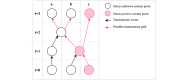
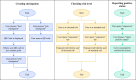
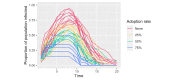
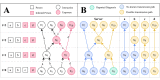
Methods: We propose the use of an anonymized graph of interpersonal interactions to conduct a novel form of contact tracing and have developed a proof-of-concept smartphone app that implements this approach. Additionally, we developed a computer simulation model that demonstrates the impact of our proposal on epidemic or pandemic outbreak trajectories across multiple rates of adoption.
Results: Our proof-of-concept smartphone app allows users to create "checkpoints" for contact tracing, check their risk level based on their past interactions, and anonymously self-report a positive status to their peer network. Our simulation results suggest that higher adoption rates of such an app may result in a better controlled epidemic or pandemic outbreak.
Conclusions: Our proposed smartphone-based contact tracing method presents a novel solution that preserves privacy while demonstrating the potential to suppress an epidemic or pandemic outbreak. This app could potentially be applied to the current COVID-19 pandemic as well as other epidemics or pandemics in the future to achieve a middle ground between drastic isolation measures and unmitigated disease spread.
Keywords: COVID-19; contact tracing; coronavirus; epidemic; mobile phone; pandemic; peer-to-peer; personal data; privacy; smartphone.
©Tyler M Yasaka, Brandon M Lehrich, Ronald Sahyouni. Originally published in JMIR mHealth and uHealth (http://mhealth.jmir.org), 07.04.2020.
Conflict of interest statement
Conflicts of Interest: None declared.
Figures
Comment in
-
Adoption of a Contact Tracing App for Containing COVID-19: A Health Belief Model Approach.JMIR Public Health Surveill. 2020 Sep 1;6(3):e20572. doi: 10.2196/20572. JMIR Public Health Surveill. 2020. PMID: 32755882 Free PMC article.
References
-
- Ferguson NM, Laydon D, Nedjati-Gilani G, Imai N, Ainslie K, Baguelin M, Bhatia S, Boonyasiri A, Cucunubá Z, Cuomo-Dannenburg G, Dighe A, Dorigatti I, Fu H, Gaythorpe K, Green W, Hamlet A, Hinsley W, Okell LC, van Elsland S, Thompson H, Verity R, Volz E, Wang H, Wang Y, Walker PGT, Walters C, Winskill P, Whittaker C, Donnelly CA, Riley S, Ghani AC. Impact of non-pharmaceutical interventions (NPIs) to reduce COVID-19 mortality and healthcare demand. Imperial College. 2020 Mar 16; https://www.imperial.ac.uk/media/imperial-college/medicine/sph/ide/gida-...
-
- Armbruster B, Brandeau ML. Contact tracing to control infectious disease: when enough is enough. Health Care Manag Sci. 2007 Dec;10(4):341–55. doi: 10.1007/s10729-007-9027-6. http://europepmc.org/abstract/MED/18074967 - DOI - PMC - PubMed
-
- Isaak J, Hanna MJ. User data privacy: Facebook, Cambridge Analytica, and privacy protection. Computer. 2018 Aug;51(8):56–59. doi: 10.1109/mc.2018.3191268. - DOI
-
- Iyengar A, Kundu A, Pallis G. Healthcare informatics and privacy. IEEE Internet Comput. 2018 Mar;22(2):29–31. doi: 10.1109/mic.2018.022021660. - DOI
MeSH terms
LinkOut - more resources
Full Text Sources
Other Literature Sources
Miscellaneous