Healthcare Data Breaches: Insights and Implications
- PMID: 32414183
- PMCID: PMC7349636
- DOI: 10.3390/healthcare8020133
Healthcare Data Breaches: Insights and Implications
Abstract
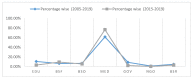
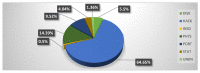
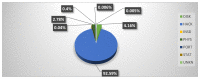
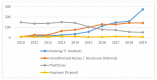
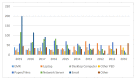
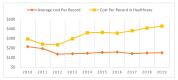
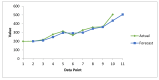
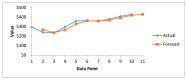
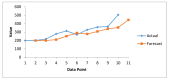
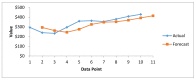
The Internet of Medical Things, Smart Devices, Information Systems, and Cloud Services have led to a digital transformation of the healthcare industry. Digital healthcare services have paved the way for easier and more accessible treatment, thus making our lives far more comfortable. However, the present day healthcare industry has also become the main victim of external as well as internal attacks. Data breaches are not just a concern and complication for security experts; they also affect clients, stakeholders, organizations, and businesses. Though the data breaches are of different types, their impact is almost always the same. This study provides insights into the various categories of data breaches faced by different organizations. The main objective is to do an in-depth analysis of healthcare data breaches and draw inferences from them, thereby using the findings to improve healthcare data confidentiality. The study found that hacking/IT incidents are the most prevalent forms of attack behind healthcare data breaches, followed by unauthorized internal disclosures. The frequency of healthcare data breaches, magnitude of exposed records, and financial losses due to breached records are increasing rapidly. Data from the healthcare industry is regarded as being highly valuable. This has become a major lure for the misappropriation and pilferage of healthcare data. Addressing this anomaly, the present study employs the simple moving average method and the simple exponential soothing method of time series analysis to examine the trend of healthcare data breaches and their cost. Of the two methods, the simple moving average method provided more reliable forecasting results.
Keywords: cost effectiveness; cost forecasting; data analysis; data breach forecasting; data confidentiality; data security; healthcare data breaches; time series analysis.
Conflict of interest statement
The authors declare no conflict of interest.
Figures
References
-
- Benefits of EHRs. [(accessed on 17 January 2020)]; Available online: https://www.healthit.gov/topic/health-it-basics/benefits-ehrs.
-
- Kamoun F., Nicho M. Human and organizational factors of healthcare data breaches: The Swiss cheese model of data breach causation and prevention. Int. J. Healthc. Inf. Syst. Inform. 2014;9:42–60. doi: 10.4018/ijhisi.2014010103. - DOI
-
- Smith T.T. Examining Data Privacy Breaches in Healthcare. [(accessed on 12 May 2020)]; Available online: https://scholarworks.waldenu.edu/cgi/viewcontent.cgi?referer=&httpsredir....
Publication types
Grants and funding
LinkOut - more resources
Full Text Sources

