A Novel Lightweight Authentication Scheme for RFID-Based Healthcare Systems
- PMID: 32867181
- PMCID: PMC7506697
- DOI: 10.3390/s20174846
A Novel Lightweight Authentication Scheme for RFID-Based Healthcare Systems
Abstract
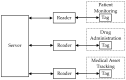
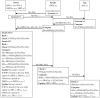
The Internet of Things (IoT) has been integrated into legacy healthcare systems for the purpose of improving healthcare processes. As one of the key technologies of IoT, radio frequency identification (RFID) technology has been applied to offer services like patient monitoring, drug administration, and medical asset tracking. However, people have concerns about the security and privacy of RFID-based healthcare systems, which require a proper solution. To solve the problem, recently in 2019, Fan et al. proposed a lightweight RFID authentication scheme in the IEEE Network. They claimed that their scheme can resist various attacks in RFID systems with low implementation cost, and thus is suitable for RFID-based healthcare systems. In this article, our contributions mainly consist of two parts. First, we analyze the security of Fan et al.'s scheme and find out its security vulnerabilities. Second, we propose a novel lightweight authentication scheme to overcome these security weaknesses. The security analysis shows that our scheme can satisfy the necessary security requirements. Besides, the performance evaluation demonstrates that our scheme is of low cost. Thus, our scheme is well-suited for practical RFID-based healthcare systems.
Keywords: authentication; healthcare systems; lightweight; radio frequency identification; security.
Conflict of interest statement
The authors declare no conflict of interest.
Figures





Similar articles
-
Enhancing Security and Privacy in Healthcare Systems Using a Lightweight RFID Protocol.Sensors (Basel). 2023 Jun 12;23(12):5518. doi: 10.3390/s23125518. Sensors (Basel). 2023. PMID: 37420689 Free PMC article.
-
Lightweight ECC based RFID authentication integrated with an ID verifier transfer protocol.J Med Syst. 2014 Oct;38(10):116. doi: 10.1007/s10916-014-0116-z. Epub 2014 Aug 6. J Med Syst. 2014. PMID: 25096968
-
A Provably Secure RFID Authentication Protocol Based on Elliptic Curve for Healthcare Environments.J Med Syst. 2016 Jul;40(7):165. doi: 10.1007/s10916-016-0521-6. Epub 2016 May 24. J Med Syst. 2016. PMID: 27221283
-
Survey: Vulnerability Analysis of Low-Cost ECC-Based RFID Protocols against Wireless and Side-Channel Attacks.Sensors (Basel). 2021 Aug 30;21(17):5824. doi: 10.3390/s21175824. Sensors (Basel). 2021. PMID: 34502714 Free PMC article. Review.
-
Survey on Prominent RFID Authentication Protocols for Passive Tags.Sensors (Basel). 2018 Oct 22;18(10):3584. doi: 10.3390/s18103584. Sensors (Basel). 2018. PMID: 30360432 Free PMC article. Review.
Cited by
-
A Survey on harnessing the Applications of Mobile Computing in Healthcare during the COVID-19 Pandemic: Challenges and Solutions.Comput Netw. 2023 Apr;224:109605. doi: 10.1016/j.comnet.2023.109605. Epub 2023 Feb 3. Comput Netw. 2023. PMID: 36776582 Free PMC article. Review.
-
A RFID Authentication Protocol for Epidemic Prevention and Epidemic Emergency Management Systems.J Healthc Eng. 2021 Dec 3;2021:1550993. doi: 10.1155/2021/1550993. eCollection 2021. J Healthc Eng. 2021. PMID: 34900176 Free PMC article.
References
-
- Chen D., Zhang N., Qin Z., Mao X., Qin Z., Shen X., Li X.Y. S2M: A Lightweight Acoustic Fingerprints-based Wireless Device Authentication Protocol. IEEE Internet Things J. 2016;4:88–100. doi: 10.1109/JIOT.2016.2619679. - DOI
-
- Granjal J., Monteiro E., Silva J.S. Security for the Internet of Things: A Survey of Existing Protocols and Open Research Issues. IEEE Commun. Surv. Tutor. 2015;17:1294–1312. doi: 10.1109/COMST.2015.2388550. - DOI
-
- Atzori L., Iera A., Morabito G. The Internet of Things: A Survey. Comput. Netw. 2010;54:2787–2805. doi: 10.1016/j.comnet.2010.05.010. - DOI
-
- Fan K., Gong Y., Liang C., Li H., Yang Y. Lightweight and Ultralightweight RFID Mutual Authentication Protocol with Cache in the Reader for IoT in 5G. Secur. Commun. Netw. 2016;9:3095–3104. doi: 10.1002/sec.1314. - DOI
-
- Juels A. RFID Security and Privacy: A Research Survey. IEEE J. Sel. Areas Commun. 2006;24:381–394. doi: 10.1109/JSAC.2005.861395. - DOI
MeSH terms
Grants and funding
- NY216016/Nanjing University of Posts and Telecommunications
- 61902196/National Natural Science Foundation of China
- 61872196/National Natural Science Foundation of China
- 61602261/National Natural Science Foundation of China
- 61672296/National Natural Science Foundation of China
- BE2017166/Scientific and Technological Support Project of Jiangsu Province
- BE2019740/Scientific and Technological Support Project of Jiangsu Province
- 18KJA520008/Major Natural Science Research Projects in Colleges and Universities of Jiangsu Province
- RJFW-111/Six Talent Peaks Project of Jiangsu Province
LinkOut - more resources
Full Text Sources
Medical
Research Materials
Miscellaneous

