Pointer Defect Detection Based on Transfer Learning and Improved Cascade-RCNN
- PMID: 32882801
- PMCID: PMC7506849
- DOI: 10.3390/s20174939
Pointer Defect Detection Based on Transfer Learning and Improved Cascade-RCNN
Abstract
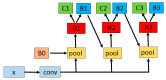
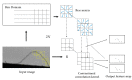
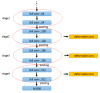
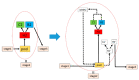
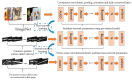
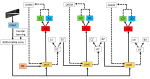
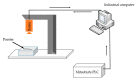
To meet the practical needs of detecting various defects on the pointer surface and solve the difficulty of detecting some defects on the pointer surface, this paper proposes a transfer learning and improved Cascade-RCNN deep neural network (TICNET) algorithm for detecting pointer defects. Firstly, the convolutional layers of ResNet-50 are reconstructed by deformable convolution, which enhances the learning of pointer surface defects by feature extraction network. Furthermore, the problems of missing detection caused by internal differences and weak features are effectively solved. Secondly, the idea of online hard example mining (OHEM) is used to improve the Cascade-RCNN detection network, which achieve accurate classification of defects. Finally, based on the fact that common pointer defect dataset and pointer defect dataset established in this paper have the same low-level visual characteristics. The network is pre-trained on the common defect dataset, and weights are transferred to the defect dataset established in this paper, which reduces the training difficulty caused by too few data. The experimental results show that the proposed method achieves a 0.933 detection rate and a 0.873 mean average precision when the threshold of intersection over union is 0.5, and it realizes high precision detection of pointer surface defects.
Keywords: defect detection; deformable convolution; online hard example mining; pointer; transfer learning.
Conflict of interest statement
The authors declare no conflict of interest.
Figures







References
-
- Li C., Zhang X., Huang Y., Tang C., Fatikow S. A novel algorithm for defect extraction and classification of mobile phone screen based on machine vision. Comput. Ind. Eng. 2020;146:106530. doi: 10.1016/j.cie.2020.106530. - DOI
-
- Zhang X., Wei L., Yuan W., Ding Z. Research on micro-crack detection method of plate heat exchanger based on machine vision. J. Electr. Eng. 2020;37:856–860.
-
- Yang M. Automatic verification method of car tire temperature and pressure meter reading based on machine vision. Autom. Instrum. 2020;6:44–47.
-
- Deshpande A.M., Telikicherla A.K., Jakkali V., Wickelhaus D.A., Kumar M., Anand S. Computer vision toolkit for non-invasive monitoring of factory floor artifacts. Procedia Manuf. 2020;48:1020–1028. doi: 10.1016/j.promfg.2020.05.141. - DOI
Grants and funding
LinkOut - more resources
Full Text Sources
Other Literature Sources

