A comprehensive survey of AI-enabled phishing attacks detection techniques
- PMID: 33110340
- PMCID: PMC7581503
- DOI: 10.1007/s11235-020-00733-2
A comprehensive survey of AI-enabled phishing attacks detection techniques
Abstract
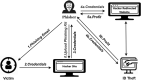
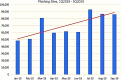
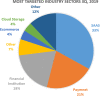
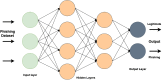
In recent times, a phishing attack has become one of the most prominent attacks faced by internet users, governments, and service-providing organizations. In a phishing attack, the attacker(s) collects the client's sensitive data (i.e., user account login details, credit/debit card numbers, etc.) by using spoofed emails or fake websites. Phishing websites are common entry points of online social engineering attacks, including numerous frauds on the websites. In such types of attacks, the attacker(s) create website pages by copying the behavior of legitimate websites and sends URL(s) to the targeted victims through spam messages, texts, or social networking. To provide a thorough understanding of phishing attack(s), this paper provides a literature review of Artificial Intelligence (AI) techniques: Machine Learning, Deep Learning, Hybrid Learning, and Scenario-based techniques for phishing attack detection. This paper also presents the comparison of different studies detecting the phishing attack for each AI technique and examines the qualities and shortcomings of these methodologies. Furthermore, this paper provides a comprehensive set of current challenges of phishing attacks and future research direction in this domain.
Keywords: Advanced phishing techniques; Cyberattack; Deep learning; Hybrid learning; Internet security; Machine learning; Phishing attack; Security threats.
© Springer Science+Business Media, LLC, part of Springer Nature 2020.
Figures

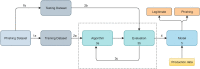
References
-
- (2016). Apwg trend report. http://docs.apwg.org/reports/apwg_trends_report_q4_2016.pdf. Accessed from 20 July 2020
-
- (2018) Phishing activity trends report. http://docs.apwg.org/reports/apwg_trends_report_q2_2018.pdf. Accessed from 20 July 2020
-
- (2019) Apwg trend report. https://docs.apwg.org/reports/apwg_trends_report_q3_2019.pdf. Accessed from 20 July 2020
-
- (2019) Fbi warns of dramatic increase in business e-mail compromise (bec) schemes—fbi. https://www.fbi.gov/contact-us/field-offices/memphis/news/press-releases.... Accessed from 20 July 2020
-
- (2019) What is phishing? https://www.phishing.org/what-is-phishing. Accessed from 20 July 2020
Publication types
LinkOut - more resources
Full Text Sources
