A New Hyperchaotic System-Based Design for Efficient Bijective Substitution-Boxes
- PMID: 33265614
- PMCID: PMC7513051
- DOI: 10.3390/e20070525
A New Hyperchaotic System-Based Design for Efficient Bijective Substitution-Boxes
Abstract
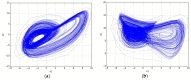
In this paper, we present a novel method to construct cryptographically strong bijective substitution-boxes based on the complicated dynamics of a new hyperchaotic system. The new hyperchaotic system was found to have good characteristics when compared with other systems utilized for S-box construction. The performance assessment of the proposed S-box method was carried out based on criteria, such as high nonlinearity, a good avalanche effect, bit-independent criteria, and low differential uniformity. The proposed method was also analyzed for the batch-generation of 8 × 8 S-boxes. The analyses found that through a proposed purely chaos-based method, an 8 × 8 S-box with a maximum average high nonlinearity of 108.5, or S-boxes with differential uniformity as low as 8, can be retrieved. Moreover, small-sized S-boxes with high nonlinearity and low differential uniformity are also obtainable. A performance comparison of the anticipated method with recent S-box proposals proved its dominance and effectiveness for a strong bijective S-box construction.
Keywords: 5-D hyperchaotic system; batch-generation; bijective; small-sized S-boxes; substitution-box.
Conflict of interest statement
The authors declare no conflict of interest.
Figures


References
-
- Knudsen L.R., Robshaw M.J. The Block Cipher Companion. Springer; Berlin/Heidelberg, Germany: 2011. Information Security and Cryptography.
-
- Shannon C.E. Communication Theory of Secrecy Systems. Bell Syst. Tech. J. 1949;28:656–715. doi: 10.1002/j.1538-7305.1949.tb00928.x. - DOI
-
- Ahmad M., Doja M.N., Beg M.M.S. ABC Optimization Based Construction of Strong Substitution-Boxes. Wirel. Pers. Commun. 2018;101:1715–1729. doi: 10.1007/s11277-018-5787-1. - DOI
-
- Makarim R.H., Tezcan C. Relating Undisturbed Bits to Other Properties of Substitution Boxes. Springer; Cham, Switzerland: 2015. pp. 109–125. Lecture Notes in Computer Science Lightweight Cryptography for Security and Privacy.
-
- Picek S., Jakobovic D., Miller J.F., Marchiori E., Batina L. Evolutionary Methods for the Construction of Cryptographic Boolean Functions. Springer; Cham, Switzerland: 2015. pp. 192–204. Lecture Notes in Computer Science Genetic Programming.
LinkOut - more resources
Full Text Sources

