Joint epitope selection and spacer design for string-of-beads vaccines
- PMID: 33381831
- PMCID: PMC7773482
- DOI: 10.1093/bioinformatics/btaa790
Joint epitope selection and spacer design for string-of-beads vaccines
Abstract
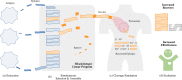
Motivation: Conceptually, epitope-based vaccine design poses two distinct problems: (i) selecting the best epitopes to elicit the strongest possible immune response and (ii) arranging and linking them through short spacer sequences to string-of-beads vaccines, so that their recovery likelihood during antigen processing is maximized. Current state-of-the-art approaches solve this design problem sequentially. Consequently, such approaches are unable to capture the inter-dependencies between the two design steps, usually emphasizing theoretical immunogenicity over correct vaccine processing, thus resulting in vaccines with less effective immunogenicity in vivo.
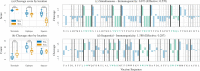
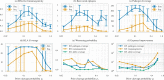
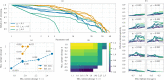
Results: In this work, we present a computational approach based on linear programming, called JessEV, that solves both design steps simultaneously, allowing to weigh the selection of a set of epitopes that have great immunogenic potential against their assembly into a string-of-beads construct that provides a high chance of recovery. We conducted Monte Carlo cleavage simulations to show that a fixed set of epitopes often cannot be assembled adequately, whereas selecting epitopes to accommodate proper cleavage requirements substantially improves their recovery probability and thus the effective immunogenicity, pathogen and population coverage of the resulting vaccines by at least 2-fold.
Availability and implementation: The software and the data analyzed are available at https://github.com/SchubertLab/JessEV.
Supplementary information: Supplementary data are available at Bioinformatics online.
© The Author(s) 2020. Published by Oxford University Press.
Figures
Similar articles
-
A multivalent minigene vaccine, containing B-cell, cytotoxic T-lymphocyte, and Th epitopes from several microbes, induces appropriate responses in vivo and confers protection against more than one pathogen.J Virol. 1997 Mar;71(3):2292-302. doi: 10.1128/JVI.71.3.2292-2302.1997. J Virol. 1997. PMID: 9032365 Free PMC article.
-
Designing string-of-beads vaccines with optimal spacers.Genome Med. 2016 Jan 26;8(1):9. doi: 10.1186/s13073-016-0263-6. Genome Med. 2016. PMID: 26813686 Free PMC article.
-
Computer-aided design of T-cell epitope-based vaccines: addressing population coverage.Int J Immunogenet. 2015 Oct;42(5):313-21. doi: 10.1111/iji.12214. Epub 2015 Jul 24. Int J Immunogenet. 2015. PMID: 26211755 Review.
-
An immunoinformatics-derived DNA vaccine encoding human class II T cell epitopes of Ebola virus, Sudan virus, and Venezuelan equine encephalitis virus is immunogenic in HLA transgenic mice.Hum Vaccin Immunother. 2017 Dec 2;13(12):2824-2836. doi: 10.1080/21645515.2017.1329788. Epub 2017 Jun 2. Hum Vaccin Immunother. 2017. PMID: 28575582 Free PMC article.
-
Epitope-driven DNA vaccine design employing immunoinformatics against B-cell lymphoma: a biotech's challenge.Biotechnol Adv. 2012 Jan-Feb;30(1):372-83. doi: 10.1016/j.biotechadv.2011.06.020. Epub 2011 Jul 2. Biotechnol Adv. 2012. PMID: 21745560 Review.
Cited by
-
Immunopeptidomics of Salmonella enterica Serovar Typhimurium-Infected Pig Macrophages Genotyped for Class II Molecules.Biology (Basel). 2024 Oct 16;13(10):832. doi: 10.3390/biology13100832. Biology (Basel). 2024. PMID: 39452141 Free PMC article.
-
A synthetic DNA template for fast manufacturing of versatile single epitope mRNA.Mol Ther Nucleic Acids. 2022 Aug 17;29:943-954. doi: 10.1016/j.omtn.2022.08.021. eCollection 2022 Sep 13. Mol Ther Nucleic Acids. 2022. PMID: 36159589 Free PMC article.
-
COVID-19 and SARS-CoV-2. Modeling the present, looking at the future.Phys Rep. 2020 Jul 10;869:1-51. doi: 10.1016/j.physrep.2020.07.005. Epub 2020 Jul 28. Phys Rep. 2020. PMID: 32834430 Free PMC article. Review.
-
Graph-theoretical formulation of the generalized epitope-based vaccine design problem.PLoS Comput Biol. 2020 Oct 23;16(10):e1008237. doi: 10.1371/journal.pcbi.1008237. eCollection 2020 Oct. PLoS Comput Biol. 2020. PMID: 33095790 Free PMC article.
References
-
- Berthold T. (2006) Primal heuristics for mixed integer programs. Master’s Thesis, Zuse Institute Berlin, Berlin, Germany.
-
- Bixby, R.E., et al. (2000) MIP: Theory and Practice — Closing the Gap. In: PowellM.J.D.ScholtesS. (eds) System Modelling and Optimization. CSMO 1999. IFIP — The International Federation for Information Processing, vol 46. Springer, Boston, MA.
-
- Brochu E. et al. (2010) A tutorial on Bayesian optimization of expensive cost functions, with application to active user modeling and hierarchical reinforcement learning. arXiv preprint arXiv:1012.2599
Publication types
MeSH terms
Substances
LinkOut - more resources
Full Text Sources
Medical

