Medical Image Protection Algorithm Based on Deoxyribonucleic Acid Chain of Dynamic Length
- PMID: 33747054
- PMCID: PMC7970129
- DOI: 10.3389/fgene.2021.654663
Medical Image Protection Algorithm Based on Deoxyribonucleic Acid Chain of Dynamic Length
Abstract
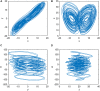
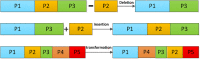
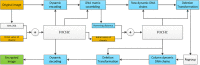
Current image encryption algorithms have various deficiencies in effectively protecting medical images with large storage capacity and high pixel correlation. This article proposed a new image protection algorithm based on the deoxyribonucleic acid chain of dynamic length, which achieved image encryption by DNA dynamic coding, generation of DNA dynamic chain, and dynamic operation of row chain and column chain. First, the original image is encoded dynamically according to the binary bit from a pixel, and the DNA sequence matrix is scrambled. Second, DNA sequence matrices are dynamically segmented into DNA chains of different lengths. After that, row and column deletion operation and transposition operation of DNA dynamic chain are carried out, respectively, which made DNA chain matrix double shuffle. Finally, the encrypted image is got after recombining DNA chains of different lengths. The proposed algorithm was tested on a list of medical images. Results showed that the proposed algorithm showed excellent security performance, and it is immune to noise attack, occlusion attack, and all common cryptographic attacks.
Keywords: DNA dynamic chain; DNA dynamic encoding; FOCHC system; deletion and transposition operation; medical image encryption.
Copyright © 2021 Xue, Jin, Zhou and Zhou.
Conflict of interest statement
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Figures







Similar articles
-
Research on Color Image Encryption Algorithm Based on Bit-Plane and Chen Chaotic System.Entropy (Basel). 2022 Jan 26;24(2):186. doi: 10.3390/e24020186. Entropy (Basel). 2022. PMID: 35205481 Free PMC article.
-
A double scrambling-DNA row and column closed loop image encryption algorithm based on chaotic system.PLoS One. 2022 Jul 12;17(7):e0267094. doi: 10.1371/journal.pone.0267094. eCollection 2022. PLoS One. 2022. PMID: 35819964 Free PMC article.
-
A Novel Chaotic Image Encryption Algorithm Based on Latin Square and Random Shift.Comput Intell Neurosci. 2021 Sep 6;2021:2091053. doi: 10.1155/2021/2091053. eCollection 2021. Comput Intell Neurosci. 2021. PMID: 34531907 Free PMC article.
-
A Symmetric Plaintext-Related Color Image Encryption System Based on Bit Permutation.Entropy (Basel). 2018 Apr 13;20(4):282. doi: 10.3390/e20040282. Entropy (Basel). 2018. PMID: 33265373 Free PMC article.
-
Image Encryption Algorithm Based on an Improved ML Neuron Model and DNA Dynamic Coding.Comput Intell Neurosci. 2022 May 14;2022:4316163. doi: 10.1155/2022/4316163. eCollection 2022. Comput Intell Neurosci. 2022. PMID: 35607463 Free PMC article.
Cited by
-
Medical image encryption algorithm based on a new five-dimensional three-leaf chaotic system and genetic operation.PLoS One. 2021 Nov 29;16(11):e0260014. doi: 10.1371/journal.pone.0260014. eCollection 2021. PLoS One. 2021. PMID: 34843485 Free PMC article.
References
-
- Akhavan A., Samsudin A., Akhshani A. (2017). Cryptanalysis of an image encryption algorithm based on DNA encoding. Optics Laser Technol. 95 94–99. 10.1016/j.optlastec.2017.04.022 - DOI
-
- Azimi Z., Ahadpour S. (2020). Color image encryption based on DNA encoding, and pair coupled chaotic maps. Multimedia Tools Appl. 79 1727–1744. 10.1007/s11042-019-08375-6 - DOI
-
- Belazi A., Hermassi H., Rhouma R., Belghith S. (2014). Algebraic analysis of a RGB image encryption algorithm based on DNA encoding, and chaotic map. Nonlin. Dyn. 76 1989–2004. 10.1007/s11071-014-1263-y - DOI
-
- Belazi A., Talha M., Kharbech S., Xiang W. (2019). Novel medical image encryption scheme based on chaos, and DNA encoding. IEEE Access. 7 36667–36681. 10.1109/ACCESS.2019.2906292 - DOI
LinkOut - more resources
Full Text Sources
Other Literature Sources