Blockchain Based Auditable Access Control for Distributed Business Processes
- PMID: 33972821
- PMCID: PMC8105781
- DOI: 10.1109/ICDCS47774.2020.00015
Blockchain Based Auditable Access Control for Distributed Business Processes
Abstract
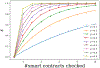
The use of blockchain technology has been proposed to provide auditable access control for individual resources. However, when all resources are owned by a single organization, such expensive solutions may not be needed. In this work we focus on distributed applications such as business processes and distributed workflows. These applications are often composed of multiple resources/services that are subject to the security and access control policies of different organizational domains. Here, blockchains can provide an attractive decentralized solution to provide auditability. However, the underlying access control policies may be overlapping in terms of the component conditions/rules, and simply using existing solutions would result in repeated evaluation of user's authorization separately for each resource, leading to significant overhead in terms of cost and computation time over the blockchain. To address this challenge, we propose an approach that formulates a constraint optimization problem to generate an optimal composite access control policy. This policy is in compliance with all the local access control policies and minimizes the policy evaluation cost over the blockchain. The developed smart contract(s) can then be deployed to the blockchain, and used for access control enforcement. We also discuss how the access control enforcement can be audited using a game-theoretic approach to minimize cost. We have implemented the initial prototype of our approach using Ethereum as the underlying blockchain and experimentally validated the effectiveness and efficiency of our approach.
Keywords: Access Control; Blockchain; Business Processes; Workflows; XACML.
Figures


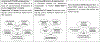
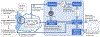





Similar articles
-
Blockchain Based Auditable Access Control For Business Processes With Event Driven Policies.IEEE Trans Dependable Secure Comput. 2024 Sep-Oct;21(5):4699-4716. doi: 10.1109/tdsc.2024.3356811. Epub 2024 Jan 22. IEEE Trans Dependable Secure Comput. 2024. PMID: 39398103 Free PMC article.
-
A Blockchain-Based Authentication and Authorization Scheme for Distributed Mobile Cloud Computing Services.Sensors (Basel). 2023 Jan 22;23(3):1264. doi: 10.3390/s23031264. Sensors (Basel). 2023. PMID: 36772304 Free PMC article.
-
Improving Diagnosis Through Digital Pathology: Proof-of-Concept Implementation Using Smart Contracts and Decentralized File Storage.J Med Internet Res. 2022 Mar 28;24(3):e34207. doi: 10.2196/34207. J Med Internet Res. 2022. PMID: 35343905 Free PMC article.
-
Blockchain Technology in the Chemical Industry.Annu Rev Chem Biomol Eng. 2022 Jun 10;13:347-371. doi: 10.1146/annurev-chembioeng-092120-022935. Epub 2022 Apr 1. Annu Rev Chem Biomol Eng. 2022. PMID: 35363506 Review.
-
Applications of Blockchain Technology for Data-Sharing in Oncology: Results from a Systematic Literature Review.Oncology. 2020;98(6):403-411. doi: 10.1159/000504325. Epub 2019 Dec 3. Oncology. 2020. PMID: 31794967
Cited by
-
Blockchain Based Auditable Access Control For Business Processes With Event Driven Policies.IEEE Trans Dependable Secure Comput. 2024 Sep-Oct;21(5):4699-4716. doi: 10.1109/tdsc.2024.3356811. Epub 2024 Jan 22. IEEE Trans Dependable Secure Comput. 2024. PMID: 39398103 Free PMC article.
-
A Service-oriented Framework for Developing Personalized Patient Care Plans for COVID-19.Proc Int Conf Digit Gov Res. 2021 Jun;2021:234-241. doi: 10.1145/3463677.3463742. Epub 2021 Jun 9. Proc Int Conf Digit Gov Res. 2021. PMID: 35224568 Free PMC article.
-
Towards Supporting Attribute-Based Access Control in Hyperledger Fabric Blockchain.IFIP Adv Inf Commun Technol. 2022 Jun;648:360-376. doi: 10.1007/978-3-031-06975-8_21. Epub 2022 Jun 3. IFIP Adv Inf Commun Technol. 2022. PMID: 36544863 Free PMC article.
References
-
- Mei H, Huang G, and Xie T, “Internetware: A software paradigm for internet computing,” Computer, vol. 45, no. 6, pp. 26–31, 2012.
-
- Afzal A, Shafiq B, Shamail S, Elahraf A, Vaidya J, and Adam NR, “Assemble: Attribute, structure and semantics based service mapping approach for collaborative business process development,” IEEE Transactions on Services Computing, 2018.
-
- Im J, Kim S, and Kim D, “Iot mashup as a service: cloud-based mashup service for the internet of things,” in 2013 IEEE International Conference on Services Computing, pp. 462–469, IEEE, 2013.
-
- Ranchal R, Bhargava B, Angin P, and Othmane LB, “Epics: A framework for enforcing security policies in composite web services,” IEEE Transactions on Services Computing, 2018.
-
- Shafiq B, Ghayyur S, Masood A, Pervaiz Z, Almutairi A, Khan F, and Ghafoor A, “Composability verification of multi-service workflows in a policy-driven cloud computing environment,” IEEE Transactions on Dependable and Secure Computing, vol. 14, pp. 478–493, September. 2017.
Grants and funding
LinkOut - more resources
Full Text Sources
