An Efficient and Accurate Iris Recognition Algorithm Based on a Novel Condensed 2-ch Deep Convolutional Neural Network
- PMID: 34071850
- PMCID: PMC8197830
- DOI: 10.3390/s21113721
An Efficient and Accurate Iris Recognition Algorithm Based on a Novel Condensed 2-ch Deep Convolutional Neural Network
Abstract
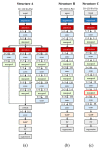
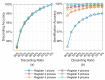
Recently, deep learning approaches, especially convolutional neural networks (CNNs), have attracted extensive attention in iris recognition. Though CNN-based approaches realize automatic feature extraction and achieve outstanding performance, they usually require more training samples and higher computational complexity than the classic methods. This work focuses on training a novel condensed 2-channel (2-ch) CNN with few training samples for efficient and accurate iris identification and verification. A multi-branch CNN with three well-designed online augmentation schemes and radial attention layers is first proposed as a high-performance basic iris classifier. Then, both branch pruning and channel pruning are achieved by analyzing the weight distribution of the model. Finally, fast finetuning is optionally applied, which can significantly improve the performance of the pruned CNN while alleviating the computational burden. In addition, we further investigate the encoding ability of 2-ch CNN and propose an efficient iris recognition scheme suitable for large database application scenarios. Moreover, the gradient-based analysis results indicate that the proposed algorithm is robust to various image contaminations. We comprehensively evaluated our algorithm on three publicly available iris databases for which the results proved satisfactory for real-time iris recognition.
Keywords: convolutional neural network; deep learning; iris recognition; network pruning; online augmentation.
Conflict of interest statement
The authors declare no conflict of interest.
Figures










References
-
- Bowyer K.W., Hollingsworth K., Flynn P.J. Image understanding for iris biometrics: A survey. Comput. Vis. Image Underst. 2008;110:281–307. doi: 10.1016/j.cviu.2007.08.005. - DOI
-
- Nguyen K., Fookes C., Jillela R., Sridharan S., Ross A. Long range iris recognition: A survey. Pattern Recognit. 2017;72:123–143. doi: 10.1016/j.patcog.2017.05.021. - DOI
-
- Sheela S., Vijaya P. Iris recognition methods-survey. Int. J. Comput. Appl. Technol. 2010;3:19–25. doi: 10.5120/729-1022. - DOI
-
- Winston J.J., Hemanth D.J. A comprehensive review on iris image-based biometric system. Soft Comput. 2019;23:9361–9384. doi: 10.1007/s00500-018-3497-y. - DOI
-
- Bonnen K., Klare B.F., Jain A.K. Component-based representation in automated face recognition. IEEE Trans. Inf. Forensics Secur. 2012;8:239–253. doi: 10.1109/TIFS.2012.2226580. - DOI
MeSH terms
Grants and funding
- No. ZR2020LZH009/Key Program of Natural Science Foundation of Shandong Province
- No. JCYJ20180305164357463/Research Funds of Science and Technology Innovation Committee of Shenzhen Municipality
- No. 11474185/National Natural Science Foundation of China
- No. 2016GGX101028/Key R&D Project of Shandong Province
LinkOut - more resources
Full Text Sources

