Pindex: Private multi-linked index for encrypted document retrieval
- PMID: 34415945
- PMCID: PMC8378705
- DOI: 10.1371/journal.pone.0256223
Pindex: Private multi-linked index for encrypted document retrieval
Abstract
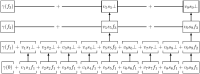
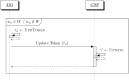
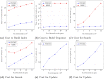
Cryptographic cloud storage is used to make optimal use of the cloud storage infrastructure to outsource sensitive and mission-critical data. The continuous growth of encrypted data outsourced to cloud storage requires continuous updating. Attacks like file-injection are reported to compromise confidentiality of the user as a consequence of information leakage during update. It is required that dynamic schemes provide forward privacy guarantees. Updates should not leak information to the untrusted server regarding the previously issued queries. Therefore, the challenge is to design an efficient searchable encryption scheme with dynamic updates and forward privacy guarantees. In this paper, a novel private multi-linked dynamic index for encrypted document retrieval namely Pindex is proposed. The multi-linked dynamic index is constructed using probabilistic homomorphic encryption mechanism and secret orthogonal vectors. Full security proofs for correctness and forward privacy in the random oracle model is provided. Experiments on real world Enron dataset demonstrates that our construction is practical and efficient. The security and performance analysis of Pindex shows that the dynamic multi-linked index guarantees forward privacy without significant loss of efficiency.
Conflict of interest statement
The authors have declared that no competing interests exist.
Figures
References
-
- Kamara S, Lauter K. Cryptographic Cloud Storage. In: Financial Cryptography and Data Security. Springer; Berlin Heidelberg; 2010. p. 136–149. Available from: https://doi.org/10.1007%2F978-3-642-14992-4_13.
-
- Bösch C, Hartel P, Jonker W, Peter A. A Survey of Provably Secure Searchable Encryption. ACM Computing Surveys. 2015;47(2):1–51.
-
- Song DX, Wagner D, Perrig A. Practical techniques for searches on encrypted data. In: Proceeding 2000 IEEE Symposium on Security and Privacy. S&P 2000. IEEE Comput. Soc;. Available from: https://doi.org/10.1109%2Fsecpri.2000.848445.
-
- Goh EJ, et al.. Secure indexes. IACR Cryptol ePrint Arch. 2003;2003:216.
-
- Curtmola R, Garay J, Kamara S, Ostrovsky R. Searchable symmetric encryption: Improved definitions and efficient constructions. Journal of Computer Security. 2011;19(5):895–934. doi: 10.3233/JCS-2011-0426 - DOI
LinkOut - more resources
Full Text Sources