A New Composite Fractal Function and Its Application in Image Encryption
- PMID: 34460663
- PMCID: PMC8321084
- DOI: 10.3390/jimaging6070070
A New Composite Fractal Function and Its Application in Image Encryption
Abstract
Fractal's spatially nonuniform phenomena and chaotic nature highlight the function utilization in fractal cryptographic applications. This paper proposes a new composite fractal function (CFF) that combines two different Mandelbrot set (MS) functions with one control parameter. The CFF simulation results demonstrate that the given map has high initial value sensitivity, complex structure, wider chaotic region, and more complicated dynamical behavior. By considering the chaotic properties of a fractal, an image encryption algorithm using a fractal-based pixel permutation and substitution is proposed. The process starts by scrambling the plain image pixel positions using the Henon map so that an intruder fails to obtain the original image even after deducing the standard confusion-diffusion process. The permutation phase uses a Z-scanned random fractal matrix to shuffle the scrambled image pixel. Further, two different fractal sequences of complex numbers are generated using the same function i.e. CFF. The complex sequences are thus modified to a double datatype matrix and used to diffuse the scrambled pixels in a row-wise and column-wise manner, separately. Security and performance analysis results confirm the reliability, high-security level, and robustness of the proposed algorithm against various attacks, including brute-force attack, known/chosen-plaintext attack, differential attack, and occlusion attack.
Keywords: composite fractal function; diffusion; henon map; permutation; random fractal matrix; z-scan.
Conflict of interest statement
The authors declare no conflict of interest.
Figures

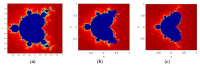
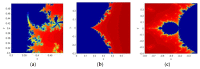
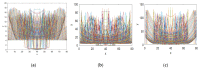
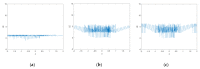






References
-
- Encyclopedia of Cryptography and Security SpringerLink. [(accessed on 18 June 2020)]; Available online: https://link.springer.com/referencework/10.1007/978-1-4419-5906-5. - DOI
-
- Smid M.E., Branstad D.K. Data Encryption Standard: Past and future. Proc. IEEE. 1988;76:550–559. doi: 10.1109/5.4441. - DOI
-
- Rivest R.L., Shamir A., Adleman L. A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM. 1978;21:120–126. doi: 10.1145/359340.359342. - DOI
-
- National Institute of Standards and technology, Advanced Encryption Standard (AES) Federal Information Processing Standard (FIPS 197) US Department of Commerce; Washington, DC, USA: 2001. - DOI
-
- Lai X., Massey J.L. Proceedings of the Workshop on the Theory and Application of Cryptographic Techniques on Advances in Cryptology (EUROCRYPT’ 90) Springer; Berlin, Heidelberg: 1991. A Proposal for a New Block Encryption Standard; pp. 389–404.
LinkOut - more resources
Full Text Sources

