Survey: Vulnerability Analysis of Low-Cost ECC-Based RFID Protocols against Wireless and Side-Channel Attacks
- PMID: 34502714
- PMCID: PMC8434319
- DOI: 10.3390/s21175824
Survey: Vulnerability Analysis of Low-Cost ECC-Based RFID Protocols against Wireless and Side-Channel Attacks
Abstract
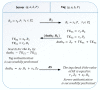
The radio frequency identification (RFID) system is one of the most important technologies of the Internet of Things (IoT) that tracks single or multiple objects. This technology is extensively used and attracts the attention of many researchers in various fields, including healthcare, supply chains, logistics, asset tracking, and so on. To reach the required security and confidentiality requirements for data transfer, elliptic curve cryptography (ECC) is a powerful solution, which ensures a tag/reader mutual authentication and guarantees data integrity. In this paper, we first review the most relevant ECC-based RFID authentication protocols, focusing on their security analysis and operational performances. We compare the various lightweight ECC primitive implementations designed for RFID applications in terms of occupied area and power consumption. Then, we highlight the security threats that can be encountered considering both network attacks and side-channel attacks and analyze the security effectiveness of RFID authentication protocols against such types of attacks. For this purpose, we classify the different threats that can target an ECC-based RFID system. After that, we present the most promising ECC-based protocols released during 2014-2021 by underlining their advantages and disadvantages. Finally, we perform a comparative study between the different protocols mentioned regarding network and side-channel attacks, as well as their implementation costs to find the optimal one to use in future works.
Keywords: ECC; RFID; SCA; attacks; cryptography; lightweight.
Conflict of interest statement
The authors declare no conflict of interest.
Figures
Similar articles
-
A secure RFID authentication protocol for healthcare environments using elliptic curve cryptosystem.J Med Syst. 2014 May;38(5):46. doi: 10.1007/s10916-014-0046-9. Epub 2014 Apr 23. J Med Syst. 2014. PMID: 24756871
-
Lightweight ECC based RFID authentication integrated with an ID verifier transfer protocol.J Med Syst. 2014 Oct;38(10):116. doi: 10.1007/s10916-014-0116-z. Epub 2014 Aug 6. J Med Syst. 2014. PMID: 25096968
-
A Novel Lightweight Authentication Scheme for RFID-Based Healthcare Systems.Sensors (Basel). 2020 Aug 27;20(17):4846. doi: 10.3390/s20174846. Sensors (Basel). 2020. PMID: 32867181 Free PMC article.
-
Survey on Prominent RFID Authentication Protocols for Passive Tags.Sensors (Basel). 2018 Oct 22;18(10):3584. doi: 10.3390/s18103584. Sensors (Basel). 2018. PMID: 30360432 Free PMC article. Review.
-
Comparison and Feasibility of Various RFID Authentication Methods Using ECC.Sensors (Basel). 2018 Sep 1;18(9):2902. doi: 10.3390/s18092902. Sensors (Basel). 2018. PMID: 30200493 Free PMC article. Review.
Cited by
-
Privacy-Aware Architectures for NFC and RFID Sensors in Healthcare Applications.Sensors (Basel). 2022 Dec 10;22(24):9692. doi: 10.3390/s22249692. Sensors (Basel). 2022. PMID: 36560061 Free PMC article.
-
A Reliable and Efficient Tracking System Based on Deep Learning for Monitoring the Spread of COVID-19 in Closed Areas.Int J Environ Res Public Health. 2021 Dec 8;18(24):12941. doi: 10.3390/ijerph182412941. Int J Environ Res Public Health. 2021. PMID: 34948549 Free PMC article.
References
-
- Rouchdi Y., El Yassini K., Oufaska K. Resolving Security and Privacy Issues in Radio Frequency Identification Middleware. Int. J. Innov. Sci. Eng. Technol. 2018;5:97–104.
-
- Alizadeh M., Zamani M., Rafiei Shahemabadi A., Shayan J., Azarnik A. A Survey on Attacks in RFID Networks. Open Int. J. Inform. 2012;1:15–24.
-
- Murugan K., Suresh P. Performance Analysis of RSA and Elliptic Curve Cryptography. Int. J. Netw. Secur. 2018;20:15.
-
- Lara-Nino C.A., Diaz-Perez A., Morales-Sandoval M. Elliptic Curve Lightweight Cryptography: A Survey. IEEE Access. 2018;6:72514–72550. doi: 10.1109/ACCESS.2018.2881444. - DOI
-
- Ibrahim A., Dalkılıc G. Review of different classes of RFID authentication protocols. Wirel. Netw. 2019;25:961–974. doi: 10.1007/s11276-017-1638-3. - DOI
Publication types
MeSH terms
LinkOut - more resources
Full Text Sources