Biometrics for Internet-of-Things Security: A Review
- PMID: 34577370
- PMCID: PMC8472874
- DOI: 10.3390/s21186163
Biometrics for Internet-of-Things Security: A Review
Abstract
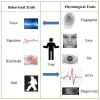
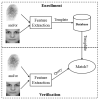
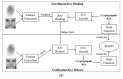
The large number of Internet-of-Things (IoT) devices that need interaction between smart devices and consumers makes security critical to an IoT environment. Biometrics offers an interesting window of opportunity to improve the usability and security of IoT and can play a significant role in securing a wide range of emerging IoT devices to address security challenges. The purpose of this review is to provide a comprehensive survey on the current biometrics research in IoT security, especially focusing on two important aspects, authentication and encryption. Regarding authentication, contemporary biometric-based authentication systems for IoT are discussed and classified based on different biometric traits and the number of biometric traits employed in the system. As for encryption, biometric-cryptographic systems, which integrate biometrics with cryptography and take advantage of both to provide enhanced security for IoT, are thoroughly reviewed and discussed. Moreover, challenges arising from applying biometrics to IoT and potential solutions are identified and analyzed. With an insight into the state-of-the-art research in biometrics for IoT security, this review paper helps advance the study in the field and assists researchers in gaining a good understanding of forward-looking issues and future research directions.
Keywords: IoT; access control; authentication; biometrics; encryption; security.
Conflict of interest statement
The authors declare no conflict of interest.
Figures

References
-
- Karie N.M., Sahri N.M., Haskell-Dowland P. IoT threat detection advances, challenges and future directions; Proceedings of the 2020 Workshop on Emerging Technologies for Security in IoT (ETSecIoT); Sydney, NSW, Australia. 21–21 April 2020; pp. 22–29.
-
- Deogirikar J., Vidhate A. Security attacks in IoT: A survey; Proceedings of the 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC); Palladam, India. 10–11 February 2017; pp. 32–37.
-
- Gurunath R., Agarwal M., Nandi A., Samanta D. An overview: Security issue in IoT network; Proceedings of the 2nd International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC); Tirunelveli, India. 29–30 October 2020; pp. 104–107.
-
- Cherapau I., Muslukhov I., Asanka N., Beznosov K. On the Impact of Touch ID on iPhone Passcodes; Proceedings of the Eleventh Symposium On Usable Privacy and Security; Pittsburgh, Pennsylvania. 20–22 July 2011; pp. 257–276.
Publication types
MeSH terms
Grants and funding
LinkOut - more resources
Full Text Sources
Research Materials

