PRASH: A Framework for Privacy Risk Analysis of Smart Homes
- PMID: 34640718
- PMCID: PMC8512241
- DOI: 10.3390/s21196399
PRASH: A Framework for Privacy Risk Analysis of Smart Homes
Abstract
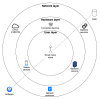
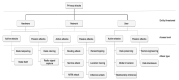
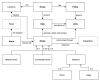
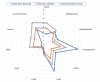
Smart homes promise to improve the quality of life of residents. However, they collect vasts amounts of personal and sensitive data, making privacy protection critically important. We propose a framework, called PRASH, for modeling and analyzing the privacy risks of smart homes. It is composed of three modules: a system model, a threat model, and a set of privacy metrics, which together are used for calculating the privacy risk exposure of a smart home system. By representing a smart home through a formal specification, PRASH allows for early identification of threats, better planning for risk management scenarios, and mitigation of potential impacts caused by attacks before they compromise the lives of residents. To demonstrate the capabilities of PRASH, an executable version of the smart home system configuration was generated using the proposed formal specification, which was then analyzed to find potential attack paths while also mitigating the impacts of those attacks. Thereby, we add important contributions to the body of knowledge on the mitigations of threat agents violating the privacy of users in their homes. Overall, the use of PRASH will help residents to preserve their right to privacy in the face of the emerging challenges affecting smart homes.
Keywords: IoT; attack taxonomy; privacy; privacy metrics; risk analysis; smart home; system model; threat model.
Conflict of interest statement
The authors declare no conflict of interest.
Figures


References
-
- Bugeja J., Jacobsson A., Davidsson P. Internet of Things A to Z. John Wiley & Sons, Ltd.; Hoboken, NJ, USA: 2018. Smart Connected Homes; pp. 359–384. Chapter 13.
-
- Zion Market Research Global Smart Home Market Worth USD 53.45 Billion by 2022. [(accessed on 19 April 2021)]. Available online: https://www.zionmarketresearch.com/news/smart-home-market.
-
- Ling Z., Luo J., Xu Y., Gao C., Wu K., Fu X. Security vulnerabilities of internet of things: A case study of the smart plug system. IEEE Internet Things J. 2017;4:1899–1909. doi: 10.1109/JIOT.2017.2707465. - DOI
-
- Notra S., Siddiqi M., Gharakheili H.H., Sivaraman V., Boreli R. An experimental study of security and privacy risks with emerging household appliances; Proceedings of the 2014 IEEE Conference on Communications and Network Security; San Francisco, CA, USA. 29–31 October 2014; pp. 79–84.
-
- Sivaraman V., Chan D., Earl D., Boreli R. Smart-phones attacking smart-homes; Proceedings of the 9th ACM Conference on Security & Privacy in Wireless and Mobile Networks; Darmstadt, Germany. 18–20 July 2016; pp. 195–200.
MeSH terms
LinkOut - more resources
Full Text Sources

