Medical image encryption algorithm based on a new five-dimensional three-leaf chaotic system and genetic operation
- PMID: 34843485
- PMCID: PMC8629275
- DOI: 10.1371/journal.pone.0260014
Medical image encryption algorithm based on a new five-dimensional three-leaf chaotic system and genetic operation
Abstract
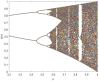
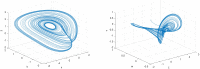
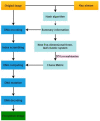
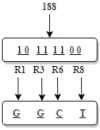
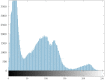
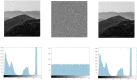
Current image encryption methods have many shortcomings for the medical image encryption with high resolution, strong correlation and large storage space, and it is difficult to obtain reliable clinically applicable medical images. Therefore, this paper proposes a medical image encryption algorithm based on a new five-dimensional three-leaf chaotic system and genetic operation. And the dynamic analysis of the phase diagram and bifurcation diagram of the five-dimensional three-leaf chaotic system selected in this paper is carried out, and NIST is used to test the randomness of its chaotic sequence. This algorithm follows the diffusion-scrambling framework, especially using the principle of DNA recombination combined with the five-dimensional three-leaf chaotic system to generate a chaotic matrix that participates in the operation. The bit-level DNA mutation operation is introduced in the diffusion, and the scrambling and diffusion effects have been further improved. Algorithm security and randomness have been enhanced. This paper evaluates the efficiency of this algorithm for medical image encryption in terms of security analysis and time performance. Security analysis is carried out from key space, information entropy, histogram, similarity between decrypted image and original image, PSNR, correlation, sensitivity, noise attack, cropping attack and so on. Perform time efficiency analysis from the perspective of time performance. The comparison between this algorithm and the experimental results obtained by some of the latest medical image encryption algorithms shows that this algorithm is superior to the existing medical image encryption algorithms to a certain extent in terms of security and time efficiency.
Conflict of interest statement
The authors have declared that no competing interests exist.
Figures









Similar articles
-
A sector fast encryption algorithm for color images based on one-dimensional composite sinusoidal chaos map.PLoS One. 2025 Jan 24;20(1):e0310279. doi: 10.1371/journal.pone.0310279. eCollection 2025. PLoS One. 2025. PMID: 39854422 Free PMC article.
-
Secured Medical Images - a Chaotic Pixel Scrambling Approach.J Med Syst. 2016 Nov;40(11):232. doi: 10.1007/s10916-016-0611-5. Epub 2016 Sep 21. J Med Syst. 2016. PMID: 27653039
-
Chaotic Image Encryption Algorithm Based on Bit Permutation and Dynamic DNA Encoding.Comput Intell Neurosci. 2017;2017:6919675. doi: 10.1155/2017/6919675. Epub 2017 Aug 22. Comput Intell Neurosci. 2017. PMID: 28912802 Free PMC article.
-
A Bit Shift Image Encryption Algorithm Based on Double Chaotic Systems.Entropy (Basel). 2021 Aug 30;23(9):1127. doi: 10.3390/e23091127. Entropy (Basel). 2021. PMID: 34573752 Free PMC article.
-
A Review on Applications of Chaotic Maps in Pseudo-Random Number Generators and Encryption.Ann Data Sci. 2022 Jan 18:1-26. doi: 10.1007/s40745-021-00364-7. Online ahead of print. Ann Data Sci. 2022. PMID: 40479176 Free PMC article. Review.
Cited by
-
An Operational DNA Strand Displacement Encryption Approach.Nanomaterials (Basel). 2022 Mar 6;12(5):877. doi: 10.3390/nano12050877. Nanomaterials (Basel). 2022. PMID: 35269365 Free PMC article.
-
A new encryption algorithm for image data based on two-way chaotic maps and iterative cellular automata.Sci Rep. 2024 Jul 19;14(1):16701. doi: 10.1038/s41598-024-64741-x. Sci Rep. 2024. PMID: 39030213 Free PMC article.
-
Enhancing AES image encryption with a three-dimensional hyperchaotic system for increased security and efficiency.PLoS One. 2025 Jul 18;20(7):e0328297. doi: 10.1371/journal.pone.0328297. eCollection 2025. PLoS One. 2025. PMID: 40680055 Free PMC article.
-
Medical image encryption algorithm based on a new five-dimensional multi-band multi-wing chaotic system and QR decomposition.Sci Rep. 2024 Jan 3;14(1):402. doi: 10.1038/s41598-023-50661-9. Sci Rep. 2024. PMID: 38172586 Free PMC article.
-
A secure medical image encryption technique based on DNA cryptography with elliptic curves.Sci Rep. 2025 Jun 6;15(1):20003. doi: 10.1038/s41598-025-03898-5. Sci Rep. 2025. PMID: 40481033 Free PMC article.
References
-
- Kengnou TAN, Fotsin HB, Kengne J. Image encryption algorithm based on dynamic DNA coding operations and 3D chaotic systems. Multimedia Tools and Applications. 2021;80(12):19011–19041. doi: 10.1007/s11042-021-10549-0 - DOI
-
- Zheng J, Liu L. Novel image encryption by combining dynamic DNA sequence encryption and the improved 2D logistic sine map. IET Image Processing. 2020;14(11):2310–2320. doi: 10.1049/iet-ipr.2019.1340 - DOI
-
- Huang X, Ye G. An image encryption algorithm based on hyper-chaos and DNA sequence. Multimedia Tools and Applications. 2012;72(1):57–70. doi: 10.1007/s11042-012-1331-6 - DOI
-
- Zhang Q, Han J, Ye Y. Multi-image encryption algorithm based on image hash, bit-plane decomposition and dynamic DNA coding. IET Image Processing. 2020;15(4):885–896. doi: 10.1049/ipr2.12069 - DOI
Publication types
MeSH terms
LinkOut - more resources
Full Text Sources

