Membership inference attacks against synthetic health data
- PMID: 34920126
- PMCID: PMC8766950
- DOI: 10.1016/j.jbi.2021.103977
Membership inference attacks against synthetic health data
Abstract
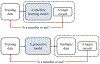
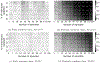
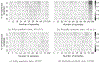
Synthetic data generation has emerged as a promising method to protect patient privacy while sharing individual-level health data. Intuitively, sharing synthetic data should reduce disclosure risks because no explicit linkage is retained between the synthetic records and the real data upon which it is based. However, the risks associated with synthetic data are still evolving, and what seems protected today may not be tomorrow. In this paper, we show that membership inference attacks, whereby an adversary infers if the data from certain target individuals (known to the adversary a priori) were relied upon by the synthetic data generation process, can be substantially enhanced through state-of-the-art machine learning frameworks, which calls into question the protective nature of existing synthetic data generators. Specifically, we formulate the membership inference problem from the perspective of the data holder, who aims to perform a disclosure risk assessment prior to sharing any health data. To support such an assessment, we introduce a framework for effective membership inference against synthetic health data without specific assumptions about the generative model or a well-defined data structure, leveraging the principles of contrastive representation learning. To illustrate the potential for such an attack, we conducted experiments against synthesis approaches using two datasets derived from several health data resources (Vanderbilt University Medical Center, the All of Us Research Program) to determine the upper bound of risk brought by an adversary who invokes an optimal strategy. The results indicate that partially synthetic data are vulnerable to membership inference at a very high rate. By contrast, fully synthetic data are only marginally susceptible and, in most cases, could be deemed sufficiently protected from membership inference.
Keywords: Contrastive representation learning; Electronic health record; Membership inference; Synthetic data.
Copyright © 2021 Elsevier Inc. All rights reserved.
Conflict of interest statement
Declaration of Competing Interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Figures
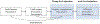



References
-
- Rubun DB, Discussion statistical disclosure limitation, Journal of Official Statistics 9 (2) (1993) 461–468. URL http://www.jos.nu/Articles/abstract.asp?article=92469
-
- Machanavajjhala A, Kifer D, Abowd J, Gehrke J, Vilhuber L, Privacy: Theory meets practice on the map, in: Proceedings - International Conference on Data Engineering, 2008, pp. 277–286. doi:10.1109/ICDE.2008.4497436. - DOI
-
- Park N, Mohammadi M, Gorde K, Jajodia S, Park H, Kim Y, Data synthesis based on generative adversarial networks, in: Proceedings of the VLDB Endowment, Vol. 11, Association for Computing Machinery, 2018, pp. 1071–1083. arXiv:1806.03384, doi:10.14778/3231751.3231757. - DOI
-
- Choi E, Biswal S, Malin B, Duke J, Stewart WF, Sun J, Generating Multi-label Discrete Patient Records using Generative Adversarial Networks, arXiv 68. arXiv:1703.06490. URL http://arxiv.org/abs/1703.06490
Publication types
MeSH terms
Grants and funding
LinkOut - more resources
Full Text Sources

